CMMC Level 1 Controls - An Introduction
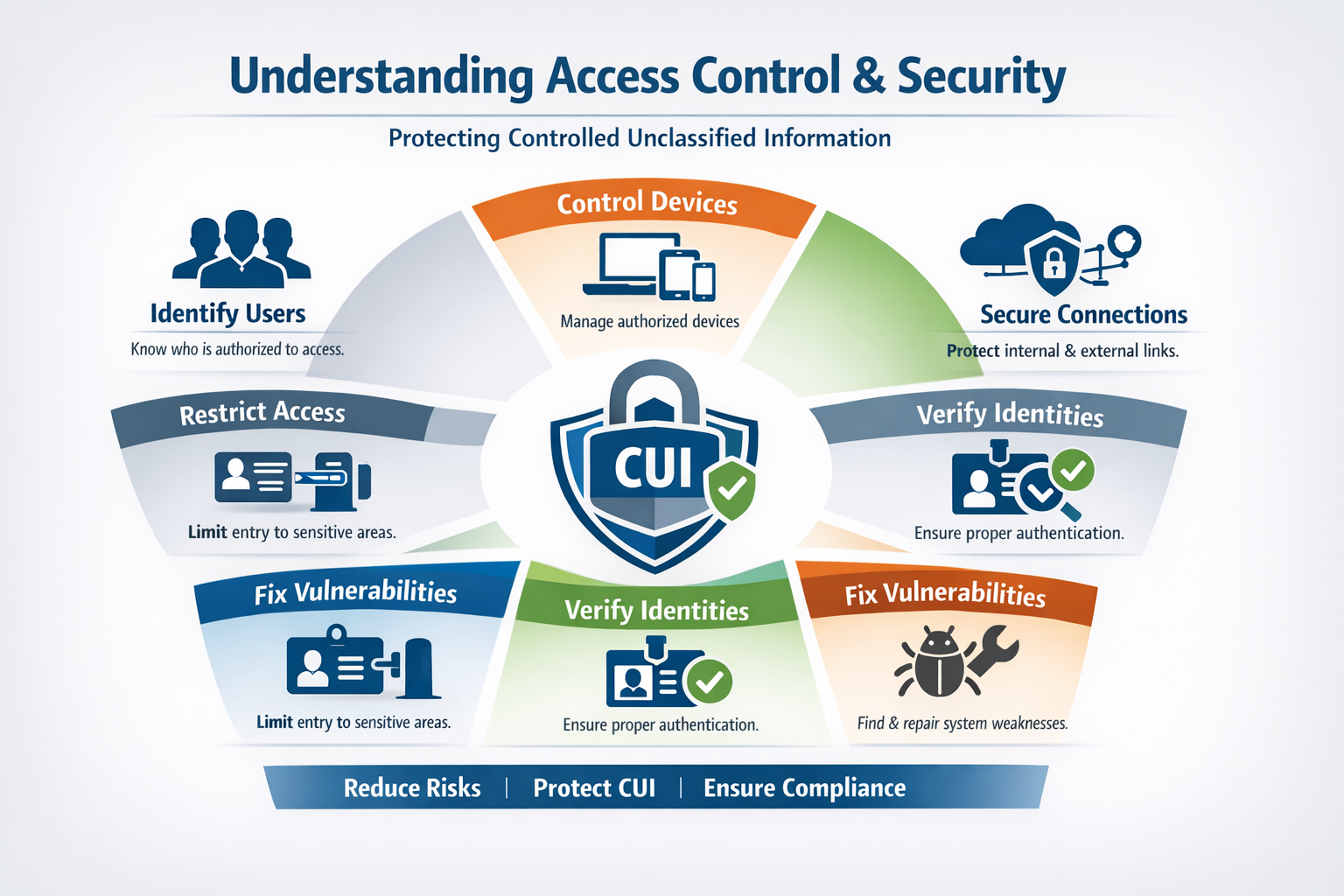
Access control and security are the foundation of protecting Controlled Unclassified Information (CUI). To meet compliance requirements, organizations must clearly define who can access their systems, what they can do, and how that access is protected. This includes users, devices, external connections, physical spaces, and even public-facing systems. In this post, we break down key security areas in simple terms to help you understand what is required and why it matters.
Access Control (AC)
- 03.01.01.a — Authorized users are identified. Additional Consideration: Is a list of authorized users maintained that defines their identities and roles [a]?
- 03.01.01.b — Processes acting on behalf of authorized users are identified.
- 03.01.01.c — Devices (including other systems) authorized to connect to the System are identified.
- 03.01.01.d — System access is limited to authorized users. Additional Consideration: Are account requests authorized before system access is granted [d,e,f]?
- 03.01.01.e — System access is limited to processes acting on behalf of authorized users. Additional Consideration: Are account requests authorized before system access is granted [d,e,f]?
- 03.01.01.f — System access is limited to authorized devices (including other systems). Additional Consideration: Are account requests authorized before system access is granted [d,e,f]?
- 03.01.02.a — The types of transactions and functions that authorized users are permitted to execute are defined. Additional Consideration: Are access control lists used to limit access to applications and data based on role and/or identity [a]?
- 03.01.02.b — System access is limited to the defined types of transactions and functions for authorized users. Additional Consideration: Is access for authorized users restricted to those parts of the system they are explicitly permitted to use (e.g., a person who only performs word-processing cannot access developer tools) [b]?
- 03.01.20.a — Connections to external systems are identified. Additional Consideration: Are all connections to external systems outside of the assessment scope identified [a]?
- 03.01.20.b — Use of external systems is identified. Additional Consideration: Are external systems (e.g., systems managed by OSAs, partners, or vendors; personal devices) that are permitted to connect to or make use of organizational systems identified [b]?
- 03.01.20.c — Connections to external systems are verified. Additional Consideration: Are methods employed to ensure that only authorized connections are being made to external systems (e.g., requiring log-ins or certificates, access from a specific IP address, or VPN) [c,e]?
- 03.01.20.d — Use of external systems is verified. Additional Consideration: Are methods employed to confirm that only authorized external systems are connecting (e.g., verifying only known/expected devices) [d]?
- 03.01.20.e — Connections to external systems are controlled/limited. Additional Consideration: Are methods employed to ensure that only authorized connections are being made to external systems [c,e]?
- 03.01.20.f — Use of external systems is controlled/limited. Additional Consideration: Is the use of external systems limited, including by policy or physical control [f]?
- 03.01.22.a — Individuals authorized to post or process information on publicly accessible systems are identified.
- 03.01.22.b — Procedures to ensure CUI is not posted or processed on publicly accessible systems are identified.
- 03.01.22.c — A review process is in place prior to posting content to publicly accessible systems. Additional Consideration: Does information on externally facing systems (i.e., publicly accessible) have a documented approval chain for public release [c]?
- 03.01.22.d — Content on publicly accessible information systems is reviewed to ensure that it does not include CUI.
- 03.01.22.e — Mechanisms are in place to remove and address improper posting of CUI.
Identification and Authentication (IA)
- 03.05.01.a — System users are identified. Additional Consideration: Are unique identifiers issued to individual users (e.g., usernames) [a]?
- 03.05.01.b — Processes acting on behalf of users are identified. Additional Consideration: Are the processes and service accounts that an authorized user initiates identified (e.g., scripts, automatic updates, configuration updates, vulnerability scans) [b]?
- 03.05.01.c — Devices accessing the System are identified. Additional Consideration: Are unique device identifiers used for devices that access the system [c]?
- 03.05.02.a — The identity of each user is authenticated or verified as a prerequisite to system access. Additional Consideration: Are unique authenticators used to verify user identities (e.g., passwords) [a]?
- 03.05.02.b — The identity of each process acting on behalf of a user is authenticated or verified as a prerequisite to system access. Additional Consideration: Are service accounts recorded and maintained for review or incident response [b]?
- 03.05.02.c — The identity of each device accessing or connecting to the System is authenticated or verified as a prerequisite to system access. Additional Consideration: Are device identifiers used in authentication processes (e.g., MAC address, non-anonymous computer name, certificates) [c]?
Media Protection (MP)
- 03.08.03.a — System media containing CUI is sanitized or destroyed before disposal. Additional Consideration: Is all managed data storage erased, encrypted, or destroyed using mechanisms to ensure that no usable data is retrievable [a,b]?
- 03.08.03.b — System media containing CUI is sanitized before it is released for reuse. Additional Consideration: Is all managed data storage erased, encrypted, or destroyed using mechanisms to ensure that no usable data is retrievable [a,b]?
Personnel Security (PE)
- 03.10.01.a — Authorized individuals allowed physical access are identified. Additional Consideration: Are lists of personnel with authorized access developed and maintained, and are appropriate authorization credentials issued [a]?
- 03.10.01.b — Physical access to organizational systems is limited to authorized individuals. Additional Consideration: Has the facility/building manager designated building areas as “sensitive” and implemented physical security protections (e.g., guards, locks, cameras, card readers) [b,c,d]?
- 03.10.01.c — Physical access to equipment is limited to authorized individuals. Additional Consideration: Has the facility/building manager designated building areas as “sensitive” and implemented physical security protections (e.g., guards, locks, cameras, card readers) [b,c,d]?
Physical Protection (PE)
- 03.10.01.d — Physical access to operating environments is limited to authorized individuals. Additional Consideration: Has the facility/building manager designated building areas as “sensitive” [b,c,d]?
- 03.10.03.a — Visitors are escorted. Additional Consideration: Are personnel required to accompany visitors to areas with physical access to organizational systems [a]?
- 03.10.03.b — Visitor activity is monitored. Additional Consideration: Are visitors clearly distinguishable from regular personnel [b]?
- 03.10.04.a — Audit logs of physical access are maintained. Additional Consideration: Are logs of physical access to sensitive areas (both authorized and visitor access) maintained per retention requirements [a]?
- 03.10.05.a — Physical access devices are identified. Additional Consideration: Are lists or inventories of physical access devices maintained (e.g., keys, facility badges, key cards) [a]?
- 03.10.05.b — Physical access devices are controlled. Additional Consideration: Is access to physical access devices limited (e.g., granted to, and accessible only by, authorized individuals) [b]?
- 03.10.05.c — Physical access devices are managed. Additional Consideration: Are physical access devices managed (e.g., revoking key card access when necessary, changing locks as needed, maintaining access control devices and systems) [c]?
System and Communications Protection (SC)
- 03.13.01.a — The external system boundary is defined. Additional Consideration: What are the external system boundary components that make up the entry and exit points for data flow (e.g., firewalls, gateways, cloud service boundaries), and what supporting components protect regulated data [a]?
- 03.13.01.b — Key internal system boundaries are defined. Additional Consideration: What internal boundary components separate key internal data flows (e.g., internal firewalls, routers, devices that bridge segments, DMZ) [b]?
- 03.13.01.c — Communications are monitored at the external system boundary. Additional Consideration: Is data flowing in and out of the external and key internal system boundaries monitored (e.g., logged, suspicious traffic alerts) [c,d]?
- 03.13.01.d — Communications are monitored at key internal boundaries. Additional Consideration: Is internal data flow monitored (e.g., logs, alerts) [c,d]?
- 03.13.01.e — Communications are controlled at the external system boundary. Additional Consideration: Are external connections denied by default and only authorized connections allowed [e,f]?
- 03.13.01.f — Communications are controlled at key internal boundaries. Additional Consideration: Are internal connections denied by default and only authorized connections allowed [e,f]?
- 03.13.01.g — Communications are protected at the external system boundary. Additional Consideration: Is data entering/leaving protected (e.g., encryption, tunneling) [g,h]?
- 03.13.01.h — Communications are protected at key internal boundaries. Additional Consideration: Is internal traffic protected (e.g., encryption, tunneling) [g,h]?
- 03.13.05.a — Publicly accessible system components are identified. Additional Consideration: Are any system components reachable by the public (e.g., internet-facing web servers, VPN gateways, publicly accessible cloud services) [a]?
- 03.13.05.b — Subnetworks for publicly accessible system components are physically or logically separated from internal networks. Additional Consideration: Are publicly accessible system components on physically or logically separated subnetworks (e.g., isolated subnetworks using separate, dedicated VLAN segments such as DMZs) [b]?
System and Information Integrity (SI)
- 03.14.01.a — The time within which to identify system flaws is specified. Additional Consideration: Is the time frame (e.g., a set number of days) within which system flaw identification activities (e.g., vulnerability scans, configuration scans, manual review) must be performed defined and documented [a]?
- 03.14.01.b — System flaws are identified within the specified time frame. Additional Consideration: Are system flaws (e.g., vulnerabilities, misconfigurations) identified in accordance with the specified time frame [b]?
- 03.14.01.c — The time within which to report system flaws is specified.
- 03.14.01.d — System flaws are reported within the specified time frame.
- 03.14.01.e — The time within which to correct system flaws is specified. Additional Consideration: Is the time frame (e.g., a set number of days dependent on the assessed severity of a flaw) within which system flaws must be corrected defined and documented [e]?
- 03.14.01.f — System flaws are corrected within the specified time frame. Additional Consideration: Are system flaws (e.g., applied security patches, made configuration changes, or implemented workarounds or mitigations) corrected in accordance with the specified time frame [f]?
- 03.14.02.a — Designated locations for malicious code protection are identified. Additional Consideration: Are system components (e.g., workstations, servers, email gateways, mobile devices) for which malicious code protection must be provided identified and documented [a]?
- 03.14.02.b — Protection from malicious code at designated locations is provided.
- 03.14.04.a — Malicious code protection mechanisms are updated when new releases are available. Additional Consideration: Is there a defined frequency by which malicious code protection mechanisms must be updated (e.g., frequency of automatic updates or manual processes) [a]?
- 03.14.05.a — The frequency for malicious code scans is defined.
- 03.14.05.b — Malicious code scans are performed with the defined frequency.
- 03.14.05.c — Real-time malicious code scans of files from external sources as files are downloaded, opened, or executed are performed. Additional Consideration: Are files from media (e.g., USB drives, CD-ROM) included in the definition of external sources and are they being scanned [c]?