SecureITSM delivers ITAR compliant infrastructure, access controls, and operational security designed for Federal contractors handling ITAR controlled technical data. We enforce U.S. person only access, export control boundaries, and continuous monitoring to protect sensitive defense data across GCC High and U.S.-based environments without compromise.


ITAR governs who can access defense-related technical data, not only whether data leaves the United States. If an unauthorized foreign person can view, administer, or indirectly access ITAR-controlled data, an export violation may already exist.
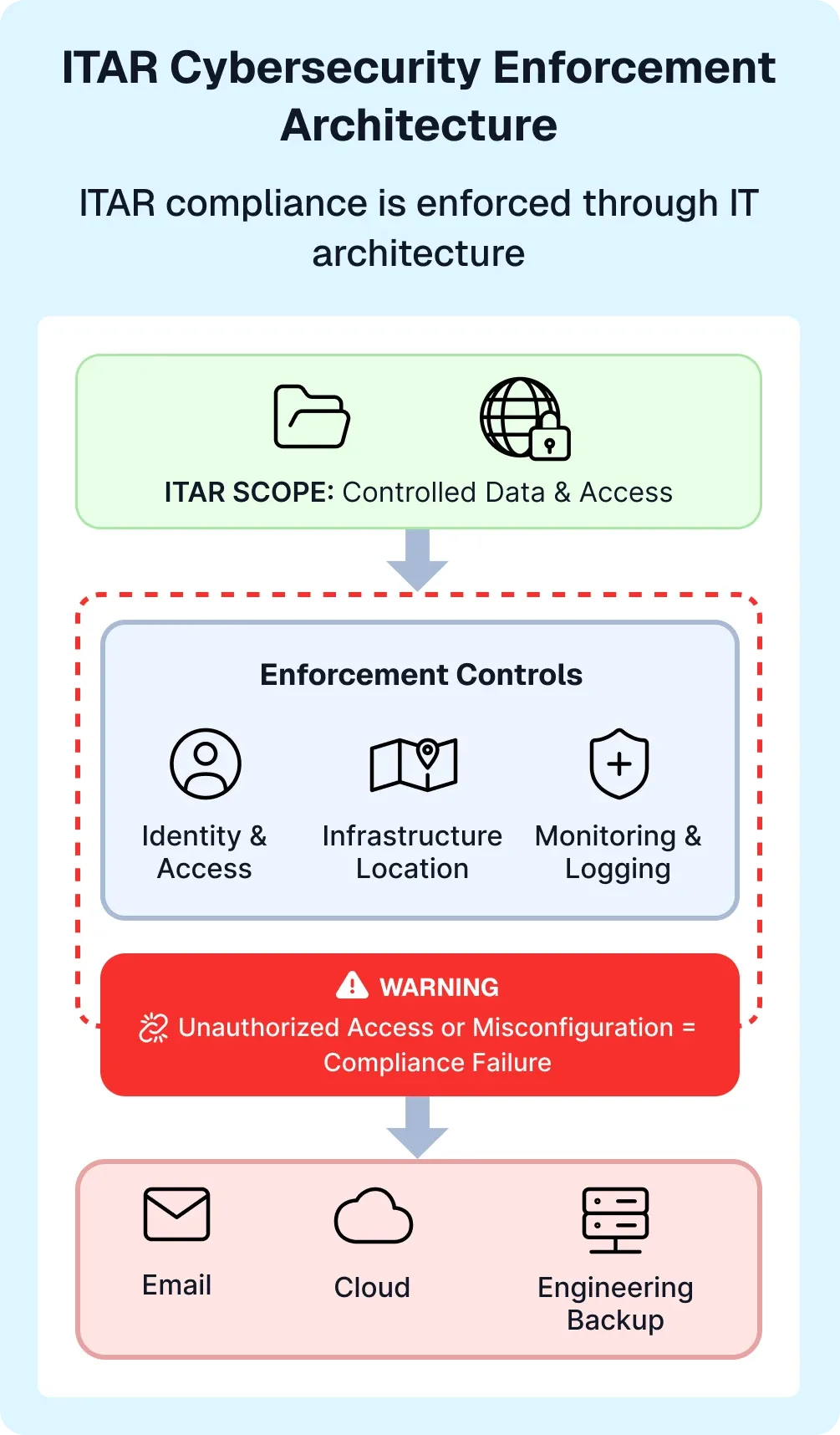
Compliance is achieved by enforcing restrictions at the identity, infrastructure, and administrative layers of your environment. Policy statements without technical enforcement do not satisfy ITAR expectations.

Email, file storage, and collaboration systems often contain drawings, specifications, and technical discussions subject to ITAR. These platforms must enforce U.S.-person-only access and administrative control.
CAD tools, PLM systems, ERP platforms, and manufacturing environments frequently store USML-related technical data. Access paths must be strictly controlled and logged.
Compliance is achieved by enforcing restrictions at the identity, infrastructure, and administrative layers of your environment. Policy statements without technical enforcement do not satisfy ITAR expectations.
ITAR obligations extend to backups, logs, and recovery platforms. If technical data is replicated, stored, or accessed elsewhere, those systems are also subject to ITAR controls.



All administrative and data access must be restricted to authorized U.S. persons. This applies to system admins, support personnel, and managed service providers.
Systems handling ITAR data must operate in approved, U.S.-based facilities with verified hosting boundaries and jurisdictional control.
Strong authentication, centralized logging, and continuous monitoring are required to demonstrate access enforcement and detect violations or misconfigurations.
Access records, configuration state, and activity logs must be retained and reviewable to demonstrate compliance during audits, investigations, or contract reviews.
ITAR violations are not hypothetical.
can constitute an export violation even without malicious intent. Penalties may include fines, contract loss, and criminal exposure.


ITAR applicability is determined by access to controlled technical data, not organizational role. Any entity with administrative, operational, or technical access to ITAR-controlled systems may b e subject to export control obligations.
Where ITAR Applies in Practice

Organizations responsible for ITAR-regulated programs must ensure all supporting systems and personnel comply with export control requirements.

ITAR applies when subcontractors access engineering data, documentation, or systems—even indirectly through shared platforms.

Systems supporting design, simulation, production, and testing often contain ITAR-controlled data and must be access-restricted accordingly.

SaaS platforms, DevOps pipelines, and cloud-hosted applications handling USML data fall within ITAR scope.

IT service providers administering environments with ITAR data must enforce U.S.-person-only access and export-control-aligned operations.
Mandatory Enforcement Areas
Only authorized U.S. persons may access ITAR-controlled systems, including all administrative functions.
System privileges must be tightly scoped, monitored, and auditable.
Data sharing platforms must enforce export control boundaries by design.
Continuous monitoring and defensible audit records are required to demonstrate compliance.
Hosting, storage, and backups must remain within approved U.S. jurisdictions.
Commercial cloud platforms are not ITAR compliant by default. ITAR-regulated environments require deliberate architectural controls to enforce U.S.-person access, tenant isolation, administrative boundaries, and export-controlled collaboration.
Standard cloud services are designed for global accessibility, shared infrastructure, and multinational administration. Without strict enforcement of identity, residency, and administrative access, commercial cloud environments introduce export-control exposure.
Commercial Microsoft 365 environments allow global administrator access, shared service planes, and multinational support models. Microsoft GCC High is architected to support U.S. government compliance requirements, but ITAR compliance still depends on how the environment is configured and operated.
ITAR-compliant cloud environments require full tenant isolation, U.S.-only administrative roles, and restricted access to management planes. Shared tenants or improperly scoped admin privileges are a common compliance failure.
Email, file sharing, and collaboration workflows must be explicitly designed to prevent uncontrolled sharing, external access, and indirect exposure to foreign persons—even within internal teams.
Most ITAR violations occur not through malicious intent, but through misconfigured systems, uncontrolled access paths, and unmanaged IT operations that expose technical data unintentionally.
Cloud administrators, MSP staff, or vendor support personnel without U.S.-person restrictions are one of the most frequent sources of ITAR violations.
Unapproved tools, shared environments, and unsanctioned cloud services bypass export controls and introduce uncontrolled data exposure.
Without centralized logging and monitoring, organizations cannot demonstrate who accessed ITAR-controlled data or when.
Protected hosting environments and U.S.-based data centers ensure secure handling of ITAR data.
Fragmented tools and undocumented configurations prevent organizations from proving compliance during audits or investigations.
From implementing ITAR-compliant infrastructure to ensuring controlled access for U.S. persons only, we deliver end-to-end solutions to keep your sensitive data secure and compliant.
Strict access controls to ensure ITAR-controlled data is only accessible to authorized U.S. persons.
All SecureITSM staff with access to ITAR-related systems are U.S. citizens with verified clearances.
We design and manage IT environments that meet export control and DFARS 252.204-7012 cybersecurity requirements.
Protected hosting environments and U.S.-based data centers ensure secure handling of ITAR data.
Maintain and manage all required ITAR compliance records, procedures, and access logs.
Continuous oversight and incident response to maintain compliance and security posture.
ITAR regulations are designed to protect defense-related technical data from unauthorized access or export. Contractors handling ITAR-controlled information must implement strict security practices, including:

Basic cyber hygiene practices for handling Federal Contract Information (FCI).
Includes basic safeguarding requirements and practices.

Implementation of all 110 security controls aligned with NIST SP 800-171 for organizations handling Controlled Unclassified Information (CUI).

Advanced/progressive controls and practices for critical CUI requiring additional protection against Advanced Persistent Threats (APTs).
Our comprehensive CMMC approach delivers measurable benefits across all aspects of compliance and security.
Typical timeline to achieve CMMC certification with our structured approach
Security staff and support resources based 100% in the United States
Complete policies, procedures, and evidence artifacts for audit readiness
U.S.-based secure data centers for ITAR-controlled information -- GCC-H
SecureITSM’s ITAR compliance experts assess your current IT environment, identify export control exposure, and design a tailored enforcement strategy aligned to ITAR requirements. ITAR compliance is not optional and it cannot be achieved through policy documents or assumptions. SecureITSM enforces export control at the system, identity, and operational level, where compliance is measured, validated, and defended.
