Achieve full NIST SP 800-171A and CMMC Level 2 control coverage with SecureITSM’s AgileDefend™ Framework, uniting GCC High tenant provisioning, Zero-Trust identity enforcement, Intune configuration baselines, Defender XDR telemetry, and Sentinel-driven evidence automation. Every safeguard is architected for CUI protection and continuous DFARS compliance.
Level 2 compliance guarantees that all technical controls, workflows, and system configurations are fully documented, tested, and mapped to your SSP and POA&M. With mandatory third-party assessment (C3PAO) for most CUI contracts, Level 2 forms the backbone of your organization’s risk reduction, operational maturity, and long-term eligibility within the Defense Industrial Base (DIB).

Every control under NIST 800-171 becomes enforceable and auditable via assessment objectives in 800-171A. Contractors must prove encryption at rest and in transit, enforce MFA across all privileged and non-privileged identities, apply device compliance with conditional access, and ingest logs into a centralized SIEM. CMMC Level 2 also demands validated configuration baselines, identity segmentation, and continuous telemetry requirements many SMB environments were never designed to support.











SecureITSM’s AgileDefend™ Level 2 Framework delivers full-stack implementation, evidence automation, and pre-audit validation mapped to every NIST 800-171A objective and DFARS 252.204-7012 requirement. We provision GCC High, enforce Zero Trust access, and deploy all 110 technical controls with automated SSP and artifact generation. Every configuration is continuously validated through Sentinel telemetry, Defender XDR enforcement, and Entra ID identity governance ensuring provable, traceable, and audit-ready CMMC Level 2 compliance.
We first analyze each customer's unique business and their corresponding IT requirements. This eliminates environment configuration mismatches minimizing the time to be audit-ready.
All 110 controls deployed across Microsoft GCC High, Intune, Defender, and Azure baseline policies, including data at rest encryption, log retention, key management, and identity segmentation.
AgileDefend™ auto-produces every policy, procedure, and artifact linked directly to NIST control numbers, DFARS 7012 reporting, and SPRS score alignment.
We operate full internal assessments including artifact review, objective validation, and auditor style questioning delivering a pre-validated environment before formal certification.
SecureITSM implements a live technical framework that proves CMMC Level 2 control execution. Every configuration, identity policy, and telemetry event is recorded, mapped, and retained for audit under DFARS 252.204-7012 requirements. Our automation process automatically correlates Sentinel logs, Defender alerts, and identity governance data into evidence-ready reporting by eliminating manual collection and audit guesswork.
Control artifacts are automatically generated, timestamped, and version-tracked inside the AgileDefend™ Evidence Manager.
Every policy, log extract, and configuration proof includes change history, ensuring defensible audit trails for C3PAO validation.
No administrator retains permanent privileges, all elevation requires approval, MFA, and time bound activation via Microsoft Entra PIM.
This delivers full traceability, eliminates standing credentials, and satisfies AC.2.007 and IA.2.078 requirements.
Microsoft Sentinel correlation rules detect DFARS-relevant events and automatically enforce the 72-hour reporting obligation defined in 252.204-7012.
Alerts feed directly into SecureITSM SOC workflows, providing forensic evidence and notification logs.
Every NIST 800-171 objective is tracked in a live pass/fail dashboard with linked evidence artifacts, remediation steps, and POA&M references.
Compliance leaders see instantly which controls are complete, in progress, or at risk with proof attached.



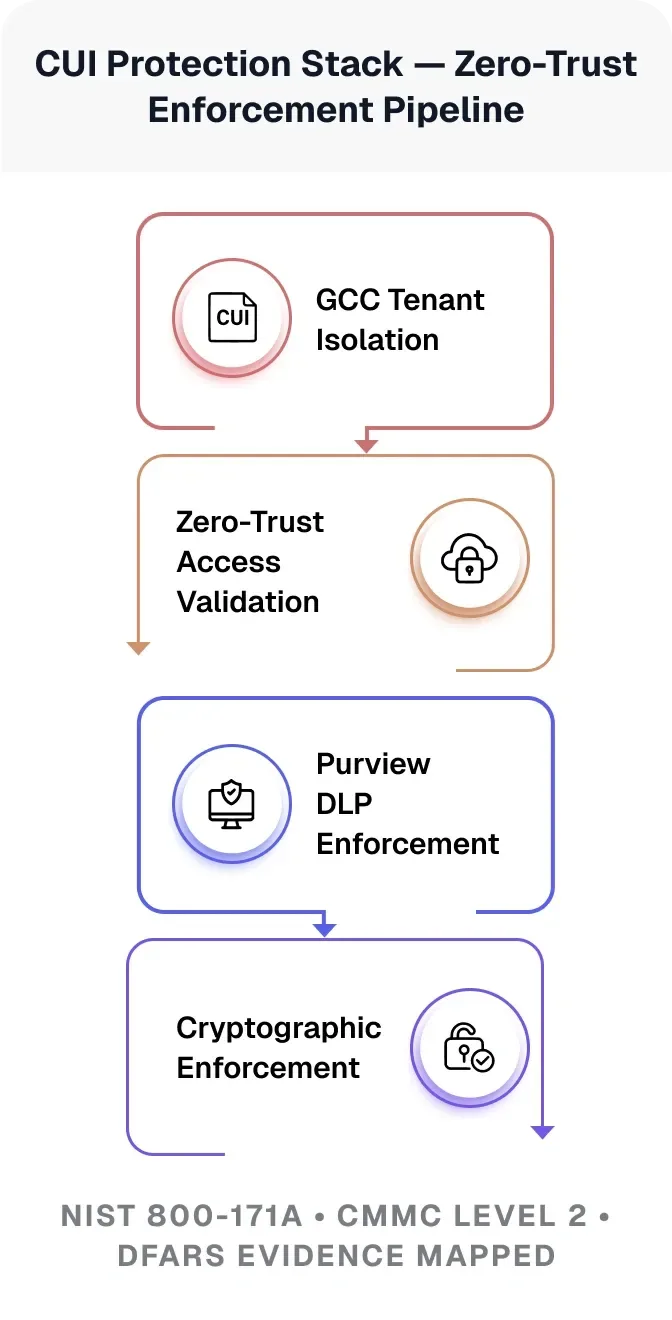
Our CUI Protection Stack applies identity-anchored encryption, sovereign cloud residency, and NIST-aligned data governance controls across every asset that touches CUI. From BitLocker-anchored device encryption to Sentinel-based exfiltration detection, every control is mapped back into the 800-171A assessment guide with live evidence capture.
All CUI workload operate inside a Microsoft 365 GCC tenant, validated through domain ownership and Microsoft approval. Boundary controls prevent lateral data leakage, cross-tenant bleed, and unauthorized administrative access. All tenant configurations align with NIST 800-171a data residency and boundary restriction requirements.
Identity access is continuously validated using device compliance posture, user risk scoring, and mandatory MFA. Microsoft Entra PIM enforces Just In Time administrative activation with no standing privileges, while adaptive policies respond dynamically to geo velocity anomalies, unmanaged devices, and session risk events.
CUI is automatically classified using Purview sensitivity labels that enforce encryption, retention, and granular sharing restrictions across Teams, SharePoint, OneDrive, and Exchange. Unauthorized downloads, forwarding, and external sharing are blocked at policy level with full audit snapshots preserved for evidence traceability.
All data at rest is encrypted using AES-256 with hardware-backed HSM key governance. TLS 1.2+ is enforced for all data in transit with continuous cipher validation and legacy protocol denial. Key rotation, cryptographic audit logs, and evidence snapshots are automatically archived and mapped to NIST 800-171A SC controls and DFARS 252.204-7012 technical requirements.
SecureITSM maintains live CMMC Level 2 compliance using continuous telemetry from Microsoft Sentinel, Defender XDR, and AgileDefend’s evidence engine. Every configuration change, policy enforcement, and security event is logged, correlated, and mapped to audit-required NIST 800-171A objectives. Compliance scores update in real time, ensuring no drift, blind spots, or undocumented deviations.

Real-time SSP-to-evidence coverage metrics, mapped to every CMMC control objective and continuously updated.

Every security alert is tagged to CMMC control families (AC, CM, IR, SI) enabling auditors to verify operational proof instantly.

Live ticket & SIEM data automatically link to DFARS 7012 and NIST 800-171A safeguards eliminating manual screenshot evidence.

SecureITSM conducts quarterly policy and evidence reviews, generating full POA&M updates and compliance score reports.
Our comprehensive CMMC approach delivers measurable benefits across all aspects of compliance and security.
Standardized GCC High provisioning pipelines ensure deterministic control deployment with <5% configuration drift risk.
XDR + SIEM + UEBA correlation ensures lateral movement, privilege abuse, and CUI exfiltration attempts are flagged within seconds.
Each of the 110 controls is implemented, validated, evidence-mapped, and measured against NIST 800-171A objective test steps.
SOC playbooks, AIR automation, and Sentinel workflow actions ensure DFARS 7012 incident response time requirements.
AC, AU, AT, CM, IA, IR, MA, MP, PE, PL, RA, RM, SA, SC, SI — fully validated and traceable inside SSP.
Identity, endpoint, cloud, and change control monitored continuously with compliance scoring dashboards.
SecureITSM delivers deterministic Level 2 compliance by implementing Zero Trust identity controls, Defender XDR telemetry, Sentinel logging pipelines, and evidence-bound SSP documentation. Every safeguard is mapped to NIST 800-171A assessment objectives and DFARS 252.204-7012 incident handling requirements. No theory , full technical enforcement with provable artifacts.
