If your contracts involve Federal Contract Information (FCI) but no Controlled Unclassified Information (CUI), you’re required to meet CMMC Level 1 through an annual self-assessment aligned to FAR 52.204-21, not a C3PAO audit. SecureITSM a CMMC MSP helps you implement the 15 safeguarding practices, document policies and procedures, and submit MET/NOT MET results with a defensible annual affirmation in SPRS. You stay eligible for DoD work while operating with strong cyber hygiene year round with no compliance gaps created by light documentation.
If your organization supports DoD contracts but does not process Controlled Unclassified Information (CUI), CMMC Level 1 applies. That means no C3PAO audit but it does require documented safeguards, annual self assessment, and formal affirmation in SPRS. Failure to protect FCI can still result in contract risk, findings, or enforcement action.
You are required to meet FAR 52.204-21 and affirm compliance annually not undergo an external audit.
Federal Contract Information includes pricing data, schedules, technical deliverables, and contract communications that must be safeguarded.
You must be able to demonstrate that controls exist, are implemented, and are operating, not just claimed.
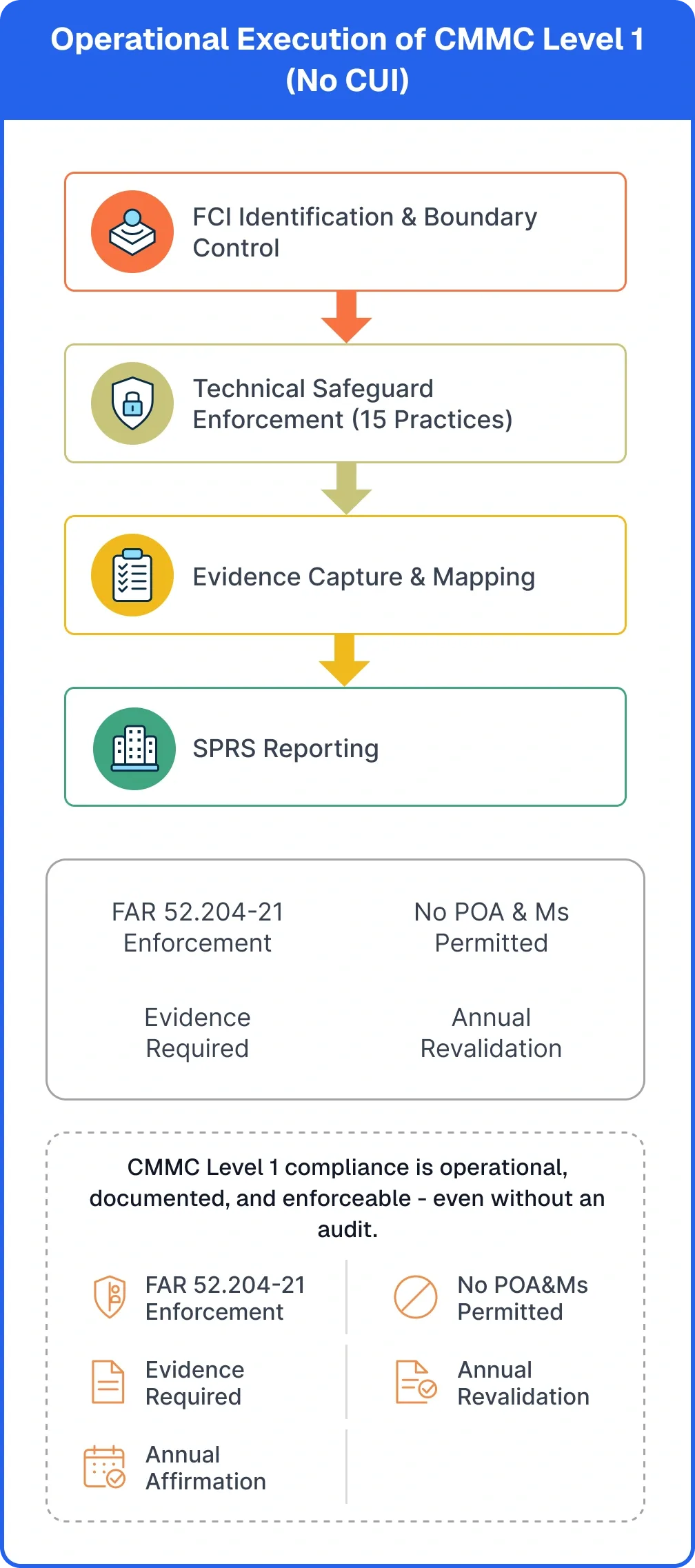
Annual self-assessment results must be accurately submitted and maintained in the Supplier Performance Risk System.
Our integrated security platform provides end-to-end protection, monitoring, and incident response capabilities to keep your business safe from evolving cyber threats.
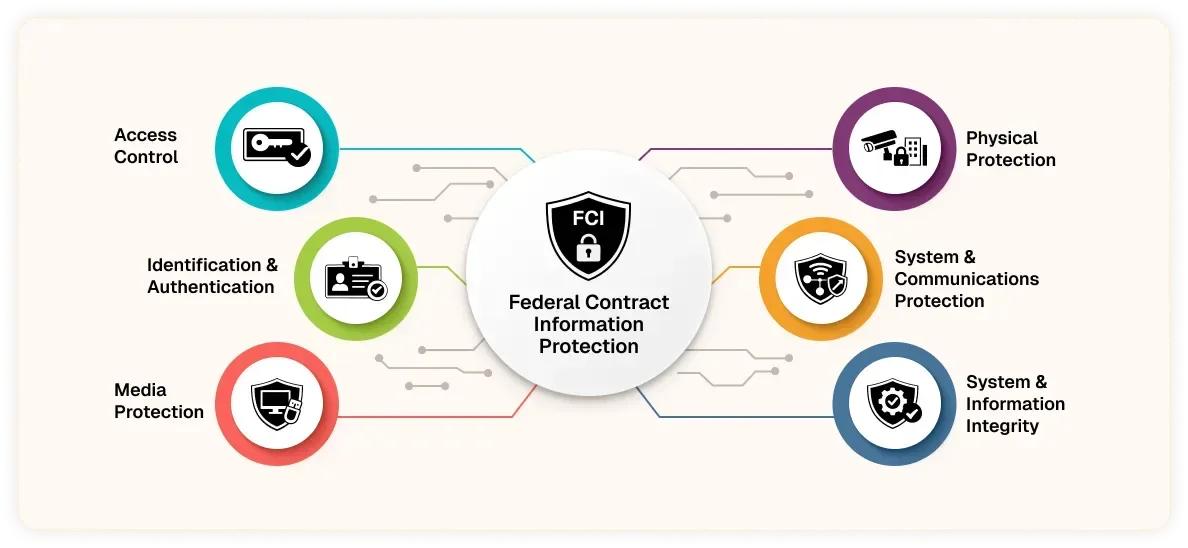
Organizations must restrict system access to authorized users, limit functions based on role, and prevent unauthorized access to FCI.
This includes account provisioning, session controls, and basic least-privilege enforcement across systems that store or transmit FCI.
Unique user identification and authentication mechanisms must be enforced for all system users.
Shared credentials, weak passwords, and unmanaged identities are non-compliant. Authentication must reliably link activity to a specific individual.
Contractors must control how removable media is used, stored, transported, and disposed of.
This includes preventing unauthorized copying of FCI and ensuring proper sanitization or destruction of media when no longer required.
Physical access to systems processing FCI must be restricted to authorized personnel.
Facilities, workstations, and devices must be protected against unauthorized physical access that could compromise FCI.
Organizations must protect FCI during transmission, enforce boundary protections, and prevent unauthorized system connections.
This includes basic network segmentation, secure communications, and protection against external access pathways.
Systems must be protected from malicious code, monitored for security alerts, and updated to correct known vulnerabilities.
Integrity controls ensure FCI is not altered, corrupted, or accessed improperly during normal operations.
While CMMC Level 1 removes the C3PAO audit requirement, it does not remove enforceable obligations under FAR 52.204-21. For many small defense contractors, the operational and compliance burden is significantly underestimated until affirmation time.
Operational Challenges Contractors Face

FCI often extends beyond obvious contract files into email communications, collaboration platforms, ticketing systems, and third-party SaaS tools.
Without a defensible system boundary, contractors risk under-protecting in-scope data or over-scoping their environment unnecessarily.

CMMC Level 1 does not allow “policy-only” compliance.
Controls must be implemented, operating, and demonstrable. If evidence is requested, internally or by the DoD contractors must be able to show configuration, access enforcement, and control execution.

Without technical validation, contractors struggle to score controls accurately.
Over-scoring creates false affirmation risk, while under-scoring can negatively impact contract eligibility. FAR 52.204-21 leaves little room for interpretation without supporting evidence.

Annual self-assessments must be correctly submitted and maintained in SPRS.
Incomplete documentation, unsupported scores, or inconsistent affirmations introduce regulatory exposure and potential contractual consequences.

Many organizations rely on spreadsheets, screenshots, and tribal knowledge.
Without a centralized compliance record tied to real system configurations, claims cannot be validated, maintained, or defended over time.
SecureITSM delivers a purpose built compliance path for DoD contractors that handle Federal Contract Information (FCI) only. Our approach eliminates unnecessary tools, reduces cost, and ensures your self-assessment and SPRS submission are technically accurate, defensible, and repeatable.
We define and validate where Federal Contract Information exists across email, file storage, collaboration tools, and systems establishing a defensible compliance boundary aligned to FAR 52.204-21.
Required policies and procedures are created and aligned directly to implemented safeguards, ensuring documentation reflects reality,not aspirational controls.
We confirm that all 15 Level 1 safeguards are fully implemented and operating, eliminating gaps that lead to false or unsupported affirmations .
Our team guides control scoring and interpretation to prevent overstatement, misclassification, or misalignment with assessment objectives.
We ensure your SPRS entry is complete, accurate, and evidence-supported reducing contractual and regulatory risk.
Senior official affirmations are backed by documented controls and repeatable processes, supporting long-term compliance sustainability.

CMMC Level 1 is not advisory. For DoD suppliers and federal subcontractors handling Federal Contract Information (FCI), it is a mandatory contractual requirement that directly affects eligibility, visibility, and accountability.
CMMC Level 1 will be embedded in new DoD contracts beginning November 10, 2025. Contractors without a valid self-assessment and SPRS submission risk disqualification during award evaluation.
Self-assessment results and affirmations are recorded in the Supplier Performance Risk System (SPRS), where they are accessible to DoD acquisition officials and primes during contract review.
Although a C3PAO audit is not required, senior official affirmation is legally binding. False or unsupported claims expose contractors to enforcement action, termination risk, and False Claims Act scrutiny.
Level 1 establishes the compliance baseline required to progress to Level 2 for contracts involving CUI. Early compliance reduces future remediation cost and schedule risk.


CMMC Level 1 compliance determines whether your organization can:
This is compliance that impacts revenue, not just security posture.
CMMC Level 1 is purpose built for DoD contractors and subcontractors that handle Federal Contract Information (FCI) but do not process Controlled Unclassified Information (CUI).

Organizations performing DoD work where FCI exists in email, files, or collaboration tools but CUI is contractually excluded. This path ensures FAR 52.204-21 compliance without unnecessary over scoping.

Engineering firms, logistics providers, IT vendors, and specialty manufacturers that must safeguard contract data while keeping operational overhead low.

Tier-2 and Tier-3 suppliers required to affirm compliance in SPRS to maintain eligibility under prime contracts and flow down requirements.

Organizations without dedicated compliance teams that still require accurate self assessments, defensible evidence, and risk-aware affirmations.
CMMC Level 1 compliance is not achieved through paperwork alone. Contractors must make targeted operational changes to ensure safeguards are implemented, understood, and consistently enforced across FCI-handling systems. To remain compliant with FAR 52.204-21 and support accurate annual affirmation, organizations must operationalize the 15 safeguarding practices, not merely document them.
Written policies and procedures must exist for all 15 safeguards and accurately reflect how controls are implemented and enforced in practice.
Personnel with access to FCI must receive basic cybersecurity training to understand access restrictions, data handling expectations, and acceptable use requirements.
Foundational IT safeguards such as access controls, authentication enforcement, endpoint protection, and boundary defenses must be active and verifiable.
Prime contractors are responsible for ensuring that FCI-handling subcontractors understand and meet Level 1 requirements where flow-down applies.
Some organizations isolate systems handling FCI to reduce compliance scope while maintaining defensible protection boundaries.
If you handle Federal Contract Information (FCI) but no Controlled Unclassified Information (CUI), CMMC Level 1 still carries enforceable obligations under FAR 52.204-21. SecureITSM helps you implement safeguards, document evidence, and submit accurate SPRS affirmations with confidence without audits, consultants, or unnecessary operational burden.
