SecureITSM delivers mission-ready IT, cybersecurity, and CMMC compliance services purpose-designed for the Defense Industrial Base meeting or exceeding CMMC requirements. Led by veteran leadership and backed by cleared engineers and Zero Trust specialists with 40+ years of DoD operational IT and Assess and Authorize experience, we help DoD contractors protect CUI, meet NIST SP 800-171, and stay CMMC Level 2 audit-ready every day.
Claudia and David Fraley have led a successful DoD contracting business since 2008, delivering U.S. Army IT operations and cybersecurity support. When DFARS 252.204-7012 introduced NIST SP 800-171 requirements, they implemented the controls in their own environment and saw the compliance burden coming for other DoD contractors. The later release of DFARS 252.204-7021 and CMMC confirmed it would be even harder—especially for small vendors.
In 2019, they launched SecureITSM as a CMMC-focused Managed IT Service Provider to help small businesses become audit-ready and sustain compliance. Today, Claudia runs Paragone Solutions, Inc., and David leads SecureITSM (a division of Paragone), supporting DoD contractors with continuous compliance through automated documentation, Zero Trust architecture, and 24×7 managed cybersecurity operations.
SecureITSM empowers DoD contractors to protect CUI and achieve CMMC Level 2 compliance through standardized Microsoft Zero Trust environments and continuous evidence generation - without enterprise budgets or in-house cybersecurity experts.
Our vision is a defense contracting ecosystem where compliance is predictable, repeatable, and affordable. By automating documentation, centralizing security operations, and standardizing environments, SecureITSM aims to make continuous CMMC readiness the norm, not an exception reserved for large enterprises.

Clarity Over Confusion: We replace vague requirements with clear, mapped, evidence-backed implementation.
Automation First: If a process can be automated, it should be—especially documentation, evidence, and compliance reporting.
Cost Discipline: We reduce C3PAO prep costs by up to 70–80% by eliminating manual effort and consultant dependency.
Proof Over Promises: Every requirement is backed by logs, configurations, policies, and traceable artifacts.
Respect for Small Businesses: CMMC should not punish contractors simply because they’re small, we design for realistic constraints.
SecureITSM is a veteran led cybersecurity and compliance partner specializing in Microsoft GCC & GCC High environments, NIST 800-171, DFARS, and CMMC Level 2 maturity. For over 16 years, our engineers, ISSOs, SOC analysts, and compliance strategists have delivered hardened, audit ready infrastructures for federal contractors who handle CUI every day.
We combine military discipline, enterprise grade engineering, and real-world operational experience to build secure, reliable, and fully traceable environments that withstand real audits. Every engagement is driven by transparency, technical rigor, and the mission to protect those who support America’s defense supply chain.

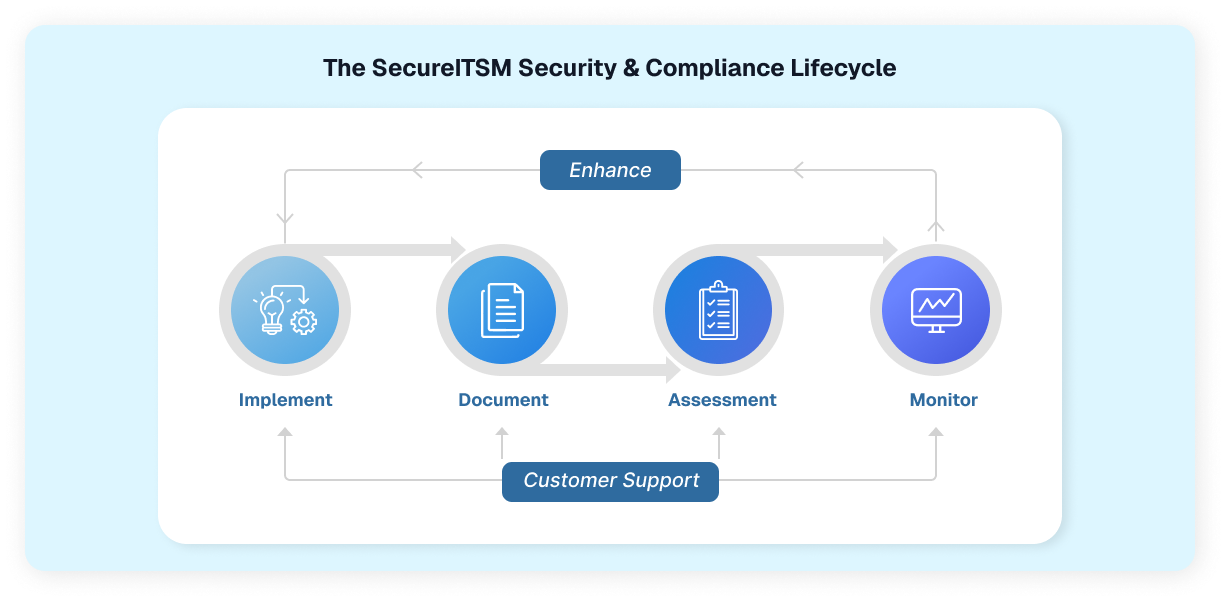
CMMC compliance is not achieved through isolated tools or one-time projects. SecureITSM delivers security through our structured, repeatable AgileDefend lifecycle that integrates assessment, system hardening, evidence automation, monitoring, and governance ensuring every control remains operational, provable, and audit-ready.
End-to-end Security Operations services designed to protect your systems and support compliance around the clock. Our SOC provides continuous monitoring, threat detection, incident response, and vulnerability management to keep your organization secure.
Build and maintain CMMC and NIST 800-171 documentation automatically. The AgileDefend™ Documentation Manager App generates SSPs, POA&Ms, and CUI data flow diagrams mapping every control to live audit evidence in real time.
CUI is automatically classified using Purview sensitivity labels that enforce encryption, retention, and granular sharing restrictions across Teams, SharePoint, OneDrive, and Exchange. Unauthorized downloads, forwarding, and external sharing are blocked at policy level with full audit snapshots preserved for evidence traceability.
SecureITSM ensures your organization remains CMMC-compliant through continuous monitoring with automated vulnerability detection, Microsoft Sentinel driven threat analytics, Defender XDR, and 24×7 monitoring. Our solution aligns with CMMC 2.0, DFARS, and NIST 800-171A standards, delivering full visibility, continuous assurance, and total control.
AgileDefend™ Enhance ensures your environment stays ahead of emerging technologies, evolving threats, and new regulatory requirements. As platforms reach end of life, standards update (such as NIST SP 800-171 Rev. 3), or adversary tactics shift, Enhance evaluates the impact, defines new control requirements, and feeds prioritized updates back into Implement for execution. Informed by insights from continuous monitoring, vulnerability trends, and compliance changes, Enhance keeps your security and compliance posture adaptive, modern, and fully aligned with future-state CMMC expectations.
AgileDefend™ Support provides 24×7 helpdesk services, Microsoft tenant management, and DFARS-aligned CMMC compliance oversight within a Zero Trust ecosystem—using ITIL processes, endpoint protection, ticket automation, and continuous monitoring to keep assets, incidents, and controls secured, documented, and audit-ready.
SecureITSM operates at the intersection of technical enforcement, compliance governance, and security operations. Our team combines certified leadership, hands on engineering expertise, and SOC driven operations delivering results that withstand scrutiny from auditors, assessors, and federal stakeholders.
CORE CAPABILITIES & ROLES

Our leadership team includes professionals holding CISSP, CGRC, and PMP certifications, bringing decades of experience across cybersecurity architecture, compliance governance, and federal program execution.
This ensures security decisions align with both technical realities and audit expectations.

Our SOC analysts provide continuous monitoring, alert triage, and incident response across cloud, identity, and endpoint environments.
This operational layer ensures security controls are not just configured but actively functioning and verifiable every day.

SecureITSM employs architects specializing in Microsoft Azure, M365 Government, and GCC High environments.
These engineers design and maintain standardized, compliant architectures that support CUI handling, enforce Zero Trust access, and generate audit ready telemetry.

Our compliance specialists translate regulatory requirements into enforceable technical and procedural controls.
They manage SSPs, POA&Ms, evidence mapping, and control validation ensuring every requirement is implemented correctly and defensibly.

SecureITSM provides ongoing risk advisory capabilities, including risk identification, scoring, mitigation tracking, and leadership reporting.
This layer supports informed decision-making and ensures compliance maturity improves over time not just at audit milestones.

Our engineers understand the operational realities of DFARS-aligned environments, including logging, incident handling, configuration control, and continuous monitoring.
This ensures technical enforcement maps directly to contractual requirements and federal expectations.








David Fraley is the Chief Technology Officer at Secure IT Service Management, Inc. (SecureITSM), guiding clients toward CMMC compliance through practical, cost-effective technology solutions. With deep expertise in IT operations, cybersecurity, and compliance, he aligns long-term strategies with NIST and DoD requirements.
A retired U.S. Army Signal Corps Officer and former Cyberwarfare Battalion Commander, he brings mission-focused leadership to every engagement. He holds CISSP, CGRC, PMP certifications, and both an MS and MBA.
Claudia Fraley is the President of Paragone Solutions, Inc. and Co-Founder of Secure IT Service Management, Inc. (SecureITSM). She brings over two decades of leadership experience in federal contracting, business strategy, and organizational development. She has a MBA.
Claudia is recognized for her strong commitment to operational excellence, team empowerment, and delivering measurable results across every engagement.
Senior IT Engineer with over a decade of experience supporting secure, mission-critical environments. Cisco Certified, with deep expertise in network infrastructure, systems administration, and cybersecurity. Spent several years in Iraq providing IT support for defense and government operations, managing complex communications networks under demanding conditions.
Known for hands-on problem solving, reliability, and the ability to maintain secure and resilient systems in any environment. He continues to apply his field-tested expertise to design, implement, and maintain high-performing IT solutions that meet both operational and compliance requirements.
An experienced IT professional with deep technical expertise across Microsoft Azure, PowerShell automation, the Microsoft Graph API, and the full Windows ecosystem. I specialize in designing, securing, and automating modern cloud and enterprise environments, with a strong focus on operational efficiency, identity management, and system hardening.
I am also a Soldier in the Army National Guard, where I hold the role of Military Intelligence Systems Maintainer/Integrator. In this capacity, I support mission-critical intelligence platforms, maintaining tactical systems, ensuring the readiness and reliability of MI systems.
Security Operations Center (SOC) Engineer with extensive experience in threat detection, incident response, and continuous monitoring across hybrid cloud and on-prem environments. Holds a Computer Science degree and brings over five years of IT experience, specializing in cybersecurity, Azure, and AWS.
Proficient in vulnerability management, including performing scans, analyzing and prioritizing findings, and coordinating remediation with system owners. Experienced in using SIEM, EDR, and vulnerability management tools to detect, investigate, and mitigate threats in real time.
CISSP with over 25 years of experience in cybersecurity and risk management. My background includes an MBA and ISO Lead Auditor certification, with specialization in CMMC, ISO audits, security architecture, penetration testing, and business continuity planning.
Throughout my career, I have focused on strengthening compliance, reducing risk, and aligning cybersecurity programs with organizational goals. I have worked directly with executives, MSPs, and MSSPs to implement practical solutions that improve resilience and support business growth in regulated industries.
Amy Sharp is Secure IT Service Management, Inc.’s (SecureITSM) Accounting Manager, overseeing full-cycle, compliant accounting operations. Her attention to detail ensures accuracy and reliability across all financial reporting, and her expertise in QuickBooks and Excel drives efficient analysis and recordkeeping.
Amy’s background spans tax, payroll, small business, and government contract accounting, supported by strong analytical and problem-solving skills. She holds an active CPA license (TN), a B.S. in Accounting, and an MBA with a concentration in accounting.
Karisa Harris is the Operations Manager at SecureITSM, overseeing daily operations, project coordination, and client service delivery. With a strong background in organizational management, she ensures projects run efficiently and align with company goals. Karisa supports leadership initiatives, drives process improvement, and helps maintain the operational excellence that defines SecureITSM’s CMMC and managed IT services.

Our comprehensive CMMC approach delivers measurable benefits across all aspects of compliance and security.
Our results are grounded in decades of hands-on experience supporting federal and defense environments. SecureITSM delivers measurable security outcomes, verified compliance, and disciplined execution that defense contractors can trust with mission critical operations.
Whether you’re preparing for CMMC, struggling with documentation, or need a trusted security partner, SecureITSM is ready to help you move forward with confidence.
