End-to-end Security Operations services designed to protect your systems and support compliance around the clock. Our SOC provides continuous monitoring, threat detection, incident response, and vulnerability management to keep your organization secure.
Each implementation follows a structured and validated sequence of steps, automating configuration, reducing audit risk, and enabling continuous compliance. Our SOC provides 24/7 monitoring and protection with advanced tools and process to protect against cyber threats.
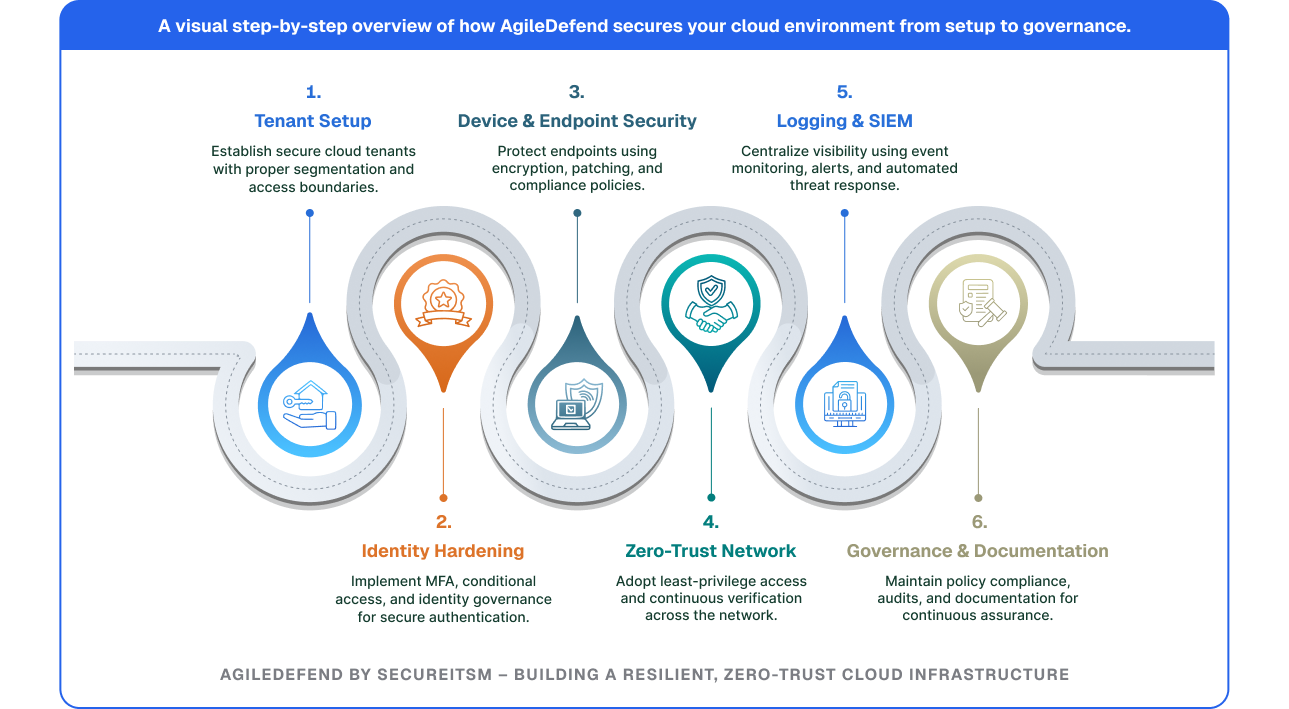
We register domains, provision Microsoft GCC or GCC High tenants, and configure secure defaults ensuring verified domain ownership, compliance boundaries, and identity isolation.
We enforce Zero-Trust access using Microsoft Entra ID applying MFA, Conditional Access policies, and Just-In-Time role activation. Including PIM configuration, identity protection automation, and hybrid sync integration for secure access governance.
SecureITSM designs segregated SharePoint and Teams structures aligned to CUI and project data boundaries. Microsoft Purview labels, retention rules, and DLP policies to enforce classification and prevent unauthorized data sharing.
We deploy Intune to manage device compliance, patching, and configuration aligning with CIS benchmarks and CMMC 2.0 control requirements. Including BitLocker, Secure Boot, Credential Guard, ASR rules, and automated patch orchestration.
Every endpoint and mailbox is protected under Defender for Endpoint and Defender for Office 365 enabling automated investigation, Safe Links, and Safe Attachments. DKIM/DMARC enforcement, phishing defense, and AIR playbooks for threat containment.
We replace traditional VPNs with compliant-device enforcement and certificate-based access using Microsoft Entra Private Access and Conditional Access policies. Azure Firewall, NSGs, DNS filtering, and remote access decommissioning.
We implement resilient backups across Microsoft 365 and Azure services with soft delete, purge protection, and Azure Key Vault encryption. Quarterly restore tests, RTO/RPO metrics, and retention compliance documentation.
We centralize all M365 and Azure logs into Microsoft Sentinel building analytics for anomaly detection, data exfiltration, and compliance dashboards. SIEM connector catalog, rule severity mapping, and integrated SOC workflows.
We maintain version control through a formal Change Control Board (CCB), ensuring every patch, image, and configuration update is logged, reviewed, and auditable. Patch compliance reports, standard image baselines, and CCB approval records.
Our comprehensive CMMC approach delivers measurable benefits across all aspects of compliance and security.
Centralized Microsoft Sentinel monitoring with custom correlation rules, EDR integration, and UEBA analytics to detect anomalies, lateral movement, and identity threats in real time.
Predefined Defender and Sentinel playbooks isolate compromised assets, trigger forensic collection, and execute remediation within minutes.
Continuous hunting powered by KQL queries and integrated threat feeds identifies hidden risks and emerging attack patterns.
Real-time dashboards, automated evidence mapping, and full audit trail documentation maintain CMMC and NIST 800-171 readiness year-round.
Defense contractors rely on AgileDefend™ to implement secure, zero-trust environments that meet CMMC and NIST standards from day one.

Raj R.CEO, , Foreign Military Sales Contractor
SecureITSM not only migrated us to Microsoft GCC High flawlessly but also securely integrated Salesforce into our controlled environment something we once thought was impossible under strict DLA data boundaries. The AgileDefend™ framework keeps our Microsoft and Salesforce systems continuously compliant and monitored, giving us complete confidence in a unified, zero-trust environment.

SecureITSM provisions and hardens Microsoft GCC or GCC High tenants, ensuring verified domain ownership, compliance boundaries, and regional data segregation.
Our team configures Azure AD, Exchange, SharePoint, and Teams with security baselines aligned to CMMC and NIST 800-171 controls enabling encrypted collaboration, secure data residency, and automated backup governance from day one.
Key Implementation Areas:
We register domains, validate DNS records, and configure secure defaults for Microsoft GCC or GCC High tenants — ensuring proper domain verification, license planning, and regional data residency compliance.

SecureITSM implements Microsoft Entra ID–based identity governance to enforce Zero-Trust principles, least privilege, and continuous access validation across your environment.
Our configuration ensures every identity human or machine is verified, monitored, and managed under strict compliance with CMMC, NIST 800-171, and DFARS requirements.
Key Implementation Areas:
Key Implementation Areas:
SecureITSM integrates IT lifecycle planning with compliance, cybersecurity, and operational resilience.
Through our AgileDefend™ framework, we translate CMMC and NIST 800-171 control requirements into measurable IT objectives ensuring every system, asset, and policy supports your long-term business and defense mission priorities
Key Implementation Areas:
We conduct monthly and quarterly vCIO sessions to align your IT roadmap with evolving DoD, DFARS, and CMMC standards. Every technology decision from cloud adoption to endpoint lifecycle is reviewed through a compliance-first lens.
We manage complete hardware and software lifecycles procurement, configuration, patching, and retirement maintaining full traceability through configuration management databases (CMDB) and automated inventory tracking.
Our strategy ensures each upgrade or migration maintains compliance alignment, supporting secure modernization within Microsoft GCC or GCC High environments while preserving audit-ready documentation.
We provide leadership dashboards tracking KPIs such as patch compliance, mean time to remediation (MTTR), and CMMC control coverage, enabling proactive risk reduction and smarter investment planning.