SecureITSM’s AgileDefend™ Application is a purpose-built CMMC compliance platform designed to remove documentation burden, formalize control inheritance, and streamline C3PAO Level 2 assessments. By aligning policies, responsibilities, risk management, and assessment artifacts in one structured system, Control Manager transforms compliance from a manual exercise into a controlled, repeatable process.

When paired with AgileDefend™ managed security services, Control ensures continuous audit readiness, not last-minute preparation.

From the customer’s perspective, SecureITSM™’s Control Manager removes the complexity of CMMC compliance by eliminating redundant work, clarifying responsibility boundaries, and automating documentation requirements. The platform is designed so customers focus only on the controls they are responsible for—while securely inheriting managed service provider (MSP) controls without having to recreate or defend them independently.
At the core of this value is structured control inheritance. MSP-implemented safeguards are formally documented, mapped, and made inheritable within the Shared Responsibility Matrix. Customers clearly see which controls are:
This eliminates duplication of effort and prevents customers from addressing controls outside their authorization boundary.
Dedicated pre-assessment preparation pages guide customers through artifact readiness, evidence validation, and objective-level review before engaging a C3PAO.
The result is a structured, assessment-ready compliance posture that reduces internal burden while increasing confidence at CMMC Level 2.
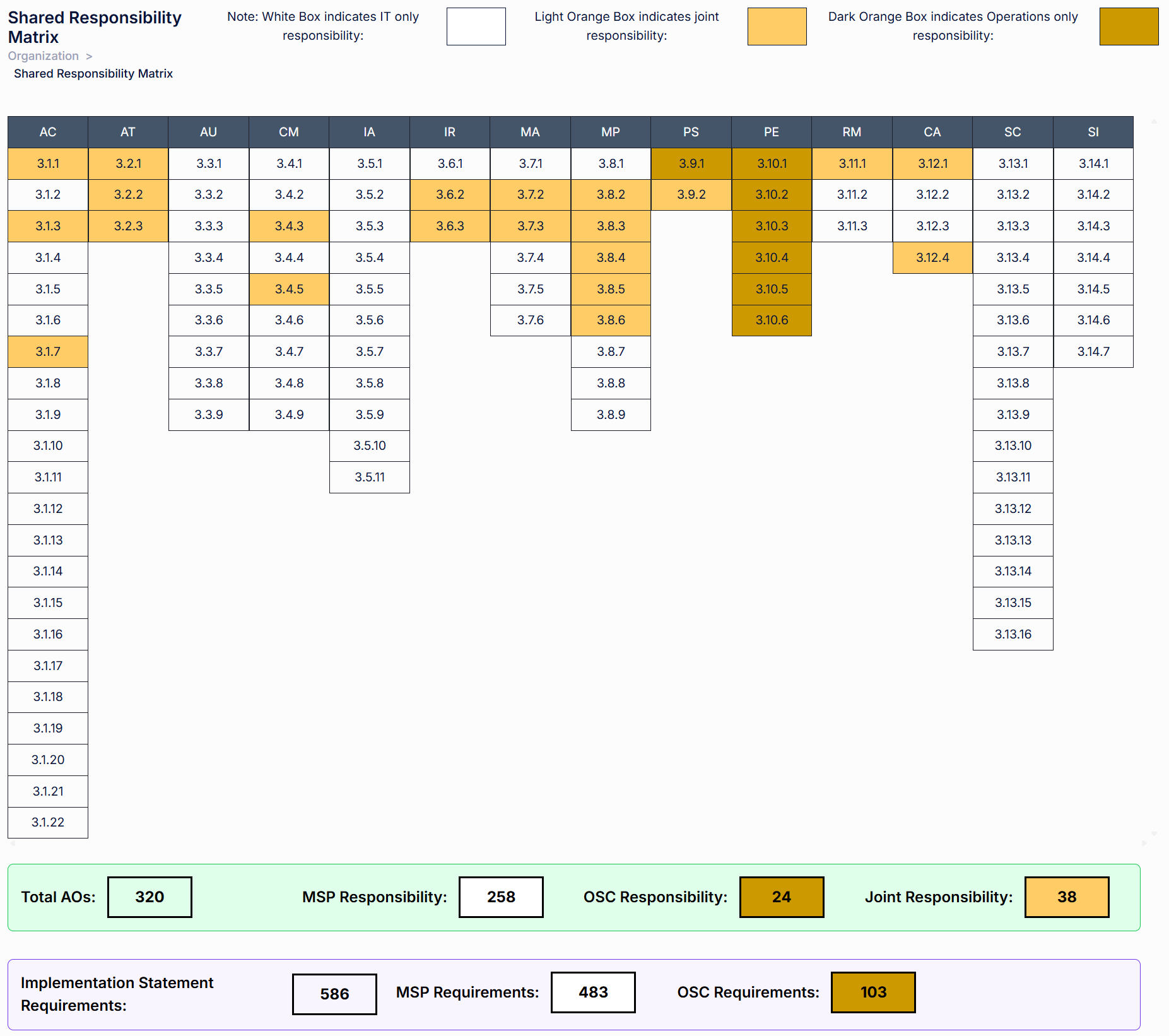
Unlike generic GRC tools, AgileDefend™ was designed specifically for CMMC. The embedded SRM provides precise, objective-level accountability mapping across all 320 CMMC Assessment Objectives and 586 implementation statements, clearly defining which responsibilities are fulfilled by the Managed Service Provider (MSP) and which remain with the organization.
Key insights from our SRM analysis:
This data-driven clarity eliminates ambiguity during assessment preparation and audit execution. Organizations gain a defensible, documented view of:
By quantifying responsibility at the assessment-objective level, AgileDefend™ reduces audit risk, prevents duplicated effort, and ensures no requirement is unintentionally unassigned.
The result is measurable transparency between client and provider, streamlined C3PAO readiness, and a defensible compliance posture built on clearly documented shared accountability.
AgileDefend™ doesn’t just store documentation — it operationalizes responsibility.
Assessment completion introduces a critical transition phase. SecureITSM supports findings documentation, evidence clarification, and POA&M coordination without guaranteeing outcomes or bypassing formal processes.
Assessment findings are organized, contextualized, and prepared for lifecycle transition without reinterpretation.
Where remediation planning is required, SecureITSM supports structured POA&M development aligned to assessment results.
We assist with evidence clarification and next-step planning without certification guarantees or assessor interference.
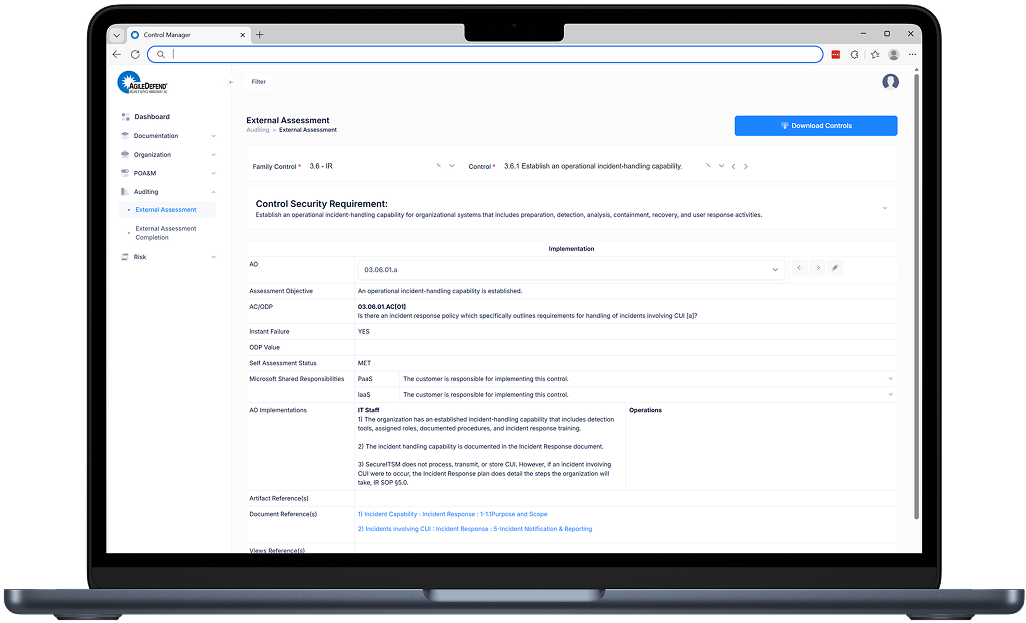
The Auditor Page serves as the authoritative assessment package, consolidating all materials required for submission to eMASS at the conclusion of a C3PAO assessment. This includes structured control narratives, implementation statements, artifact references, objective-level evidence mapping, POA&M entries, and associated assessment results.
At assessment completion, Control Manager automatically generates the required cryptographic hash record for submission, ensuring artifact integrity and compliance with DoD validation requirements.
By maintaining continuous assessment readiness, enabling structured control inheritance, and automating final submission outputs, Control Manager transforms CMMC from a disruptive, point-in-time audit event into a controlled, repeatable compliance process aligned with SecureITSM’s AgileDefend™ lifecycle methodology.
CMMC certification depends on proof of intent, process, and consistency. Strong security controls without defensible documentation routinely fail assessments.
Key to our model is our application, audit automation, and hands-on guidance throughout the audit process. SecureITSM replaces ad-hoc consulting with standardized workflows, automation, and an enforcement-driven operating model.

Evidence handling, tracking, and coordination are system-driven not spreadsheet-based.

Every assessment follows the same repeatable process reducing variance and confusion.

Controls, evidence, and operations are governed through a centralized enforcement engine.
SecureITSM delivers structured, audit-aligned CMMC assessment support covering evidence, assessor interaction, and post-assessment continuity. Defined by methodical, standards driven execution without shortcuts or assurances.