SecureITSM ensures your organization remains CMMC-compliant through continuous monitoring with automated vulnerability detection, Microsoft Sentinel driven threat analytics, Defender XDR, and 24×7 monitoring. Our solution aligns with CMMC 2.0, DFARS, and NIST 800-171A standards, delivering full visibility, continuous assurance, and total control.
AgileDefend™ monitoring provides continuous SOC-as-a-Service for defense and federal contractors. Powered by Microsoft Sentinel and Defender XDR, our monitoring aligns with CMMC Level 2 and DFARS 252.204-7012 to provide unified visibility across endpoints, identities, cloud workloads, and data flows ensuring your systems remain both secure and audit-ready at all times.
Live dashboards track vulnerabilities, configuration drift, and compliance scores across GCC High tenants, keeping every control validated.
Custom Sentinel correlation rules and automated playbooks turn raw logs into prioritized, auditable alerts with rapid triage
Defender XDR analytics detect privilege misuse and lateral movement across hybrid assets isolating threats before impact.
Executive dashboards map telemetry to CMMC & DFARS controls, providing instant audit-readiness metrics and POA&M progress.
AgileDefend™ integrates Microsoft Defender Vulnerability Management, Azure Security Center, and custom Sentinel analytics to continuously identify, score, and validate risks across your CMMC environment. Each vulnerability is mapped to NIST 800-171A objectives, with automated patch verification and residual risk modeling.

Continuous scanning and prioritized remediation insights mapped to CMMC & DFARS controls.

Centralized patch oversight ensures CIS- and DoD-compliant update enforcement.

Identify misconfigurations across cloud, network, and device baselines before compliance drift occurs.

Quantify and track residual risk with real-time dashboards aligned to your CMMC SSP objectives.
AgileDefend™ delivers a unified Continuous Monitoring Framework that validates every control, automates evidence generation, and enforces compliance boundaries within Microsoft GCC High. Built on the DoD Continuous Monitoring Plan model, our automation engine continuously verifies configurations, telemetry, and system integrity ensuring ongoing CMMC Level 2 and DFARS 252.204-7012 compliance.
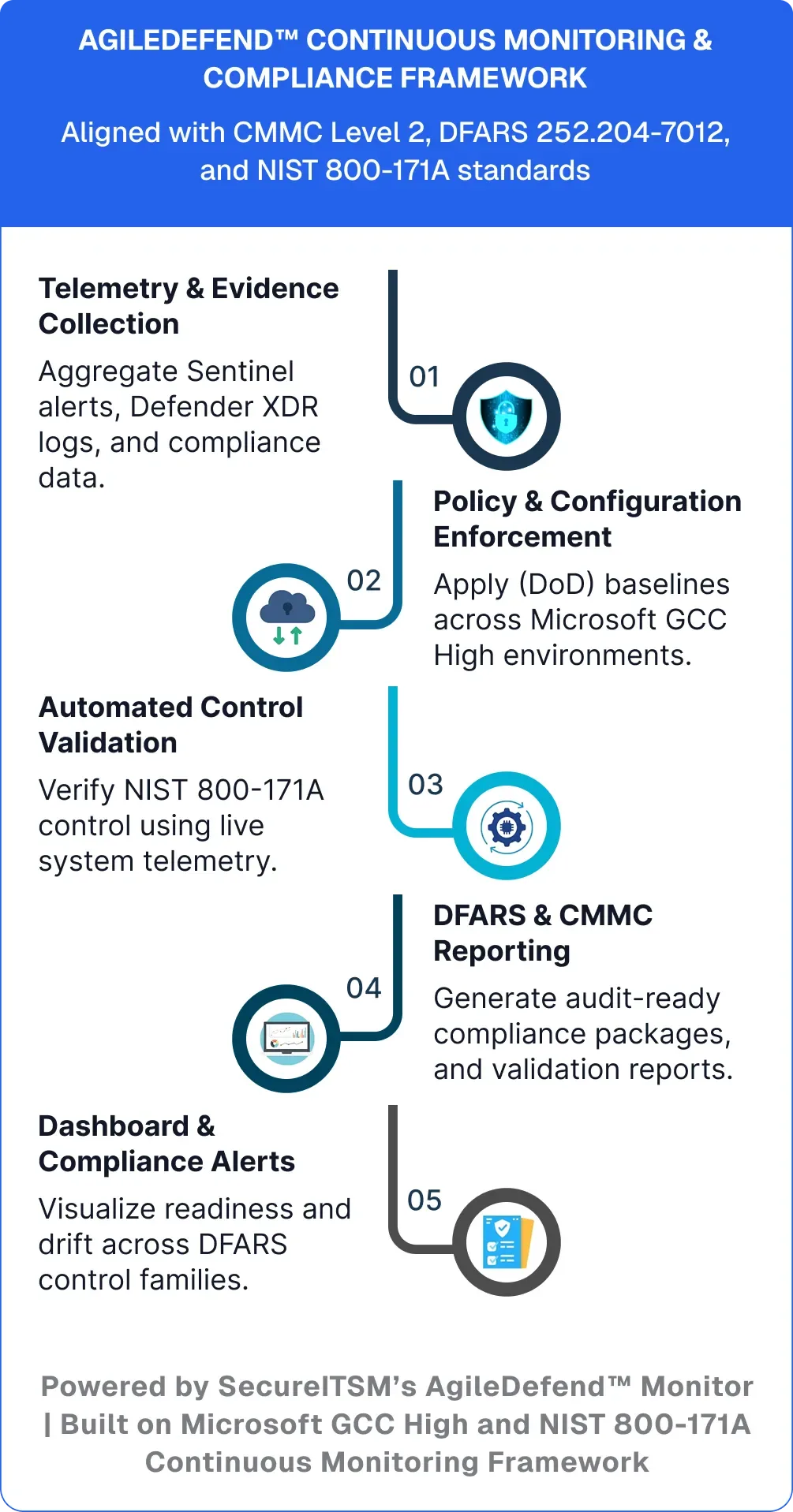
Detect configuration drift, expired evidence, or control failure in real time.
Validate telemetry across identity, endpoint, data, and network layers for always-on assurance.
View live compliance posture, risk heatmaps, and readiness indicators in executive dashboards.
Structured to meet DFARS and CMMC Level 2 continuous validation standards.
Maintain secure enclaves and data flow boundaries across Microsoft GCC High environments.
Every control objectively verified and mapped to SSP evidence libraries automatically.
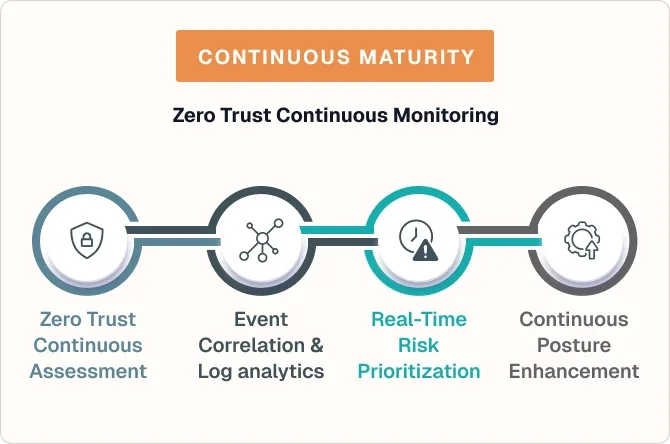
AgileDefend™ extends NIST SP 800-137 continuous monitoring principles into Zero Trust continuous assessment. By merging real-time telemetry, event analytics, and policy enforcement, organizations achieve a state of adaptive, measurable compliance maturity.


Every endpoint, session, and data access request is evaluated against dynamic policy baselines. AgileDefend™ integrates with Microsoft Entra ID and Sentinel for adaptive control validation.


Aggregate SIEM data from hybrid systems to identify control drift and insider anomalies. Log analytics reveal behavioral patterns that indicate security posture degradation.


Use data-driven scoring to quantify residual risk against NIST 800-171A controls, guiding focused remediation efforts across technical and procedural domains.


Track maturity through iterative improvement cycles, evidence validation, and Zero Trust policy tuning that evolves with each compliance review.
Our comprehensive CMMC approach delivers measurable benefits across all aspects of compliance and security.
AgileDefend™ Monitor delivers ongoing visibility across every control, risk, and endpoint ensuring DFARS and CMMC Level 2 compliance without interruption.
