Introduction
The Cybersecurity Maturity Model Certification (CMMC) has quickly become a cornerstone of cybersecurity compliance for defense contractors. Originally introduced by the U.S. Department of Defense (DoD) in 2020, the framework was designed to standardize and strengthen cybersecurity practices across the Defense Industrial Base (DIB). With the release of CMMC 2.0, the DoD has streamlined the model, making significant changes that defense contractors must fully understand in order to remain compliant and competitive in government contracting.
In this post, we’ll provide a comprehensive analysis of the CMMC 2.0 requirements, break down the differences from the original framework, and explain what defense contractors need to do to prepare for upcoming assessments.
Why CMMC 2.0 Matters
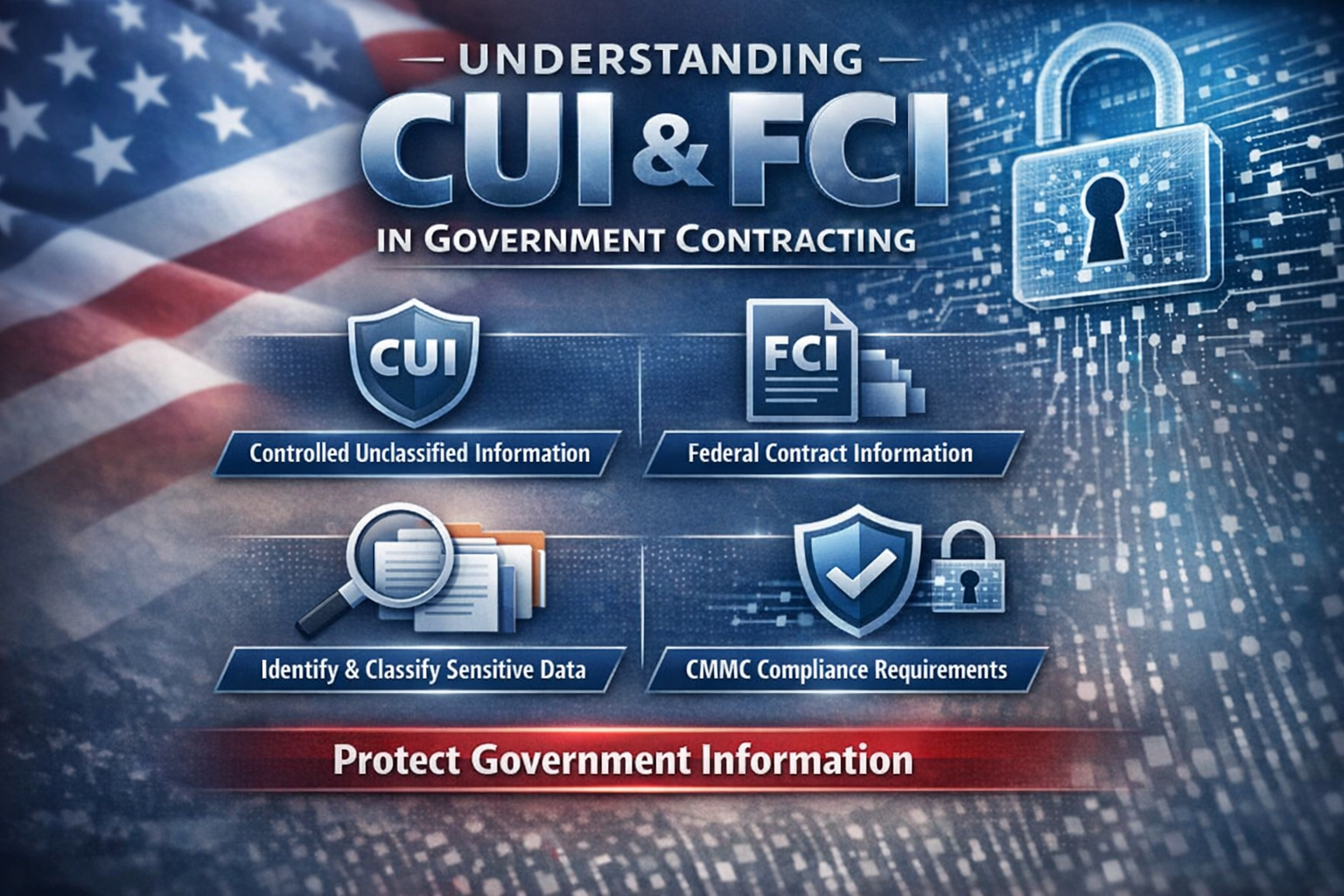
The DIB is a prime target for adversaries due to the sensitive nature of Controlled Unclassified Information (CUI) and Federal Contract Information (FCI). The DoD estimates that billions of dollars are lost annually through cyber theft and espionage. CMMC was introduced to reduce this risk, ensuring that every contractor, whether a prime or sub, meets cybersecurity standards appropriate for the type of information they handle.
With CMMC 2.0, the DoD has refined its approach to balance security, cost, and practicality. The updated model simplifies compliance without reducing the protection of sensitive information. For contractors, this means fewer barriers to entry but also increased accountability when it comes to self-attestation and audits.
Key Changes in CMMC 2.0
1. Reduction from Five Levels to Three
The most significant change is the reduction of compliance levels:
- Level 1 (Foundational): Basic safeguarding of FCI, aligned with FAR 52.204-21.
- Level 2 (Advanced): Protects CUI, aligned with NIST SP 800-171 requirements.
- Level 3 (Expert): Focused on advanced cybersecurity practices for protecting highly sensitive CUI, aligned with a subset of NIST SP 800-172.
By reducing levels, the DoD has made the framework easier to navigate, eliminating redundancy while aligning more closely with existing NIST standards.
2. Alignment with NIST Standards
CMMC 2.0 integrates directly with NIST SP 800-171 (for Level 2) and NIST SP 800-172 (for Level 3). This change ensures consistency across federal compliance requirements and reduces confusion for organizations already working toward NIST alignment.
3. Assessment Adjustments
Under the original model, third-party assessments were required at nearly every level. With CMMC 2.0:
- Level 1: Annual self-assessments are permitted.
- Level 2: Some contractors (based on sensitivity of CUI) may conduct annual self-assessments, while others must undergo third-party assessments every three years.
- Level 3: All contractors will undergo government-led assessments.
This adjustment helps reduce cost and administrative burden for small- to mid-sized contractors while still ensuring accountability for those handling sensitive data.
4. Introduction of Waivers
In rare cases where mission-critical operations demand flexibility, the DoD may grant temporary waivers. However, contractors should not expect waivers to become a standard practice as they are intended only for exceptional situations.
5. Stronger Enforcement of False Claims
Self-attestation under CMMC 2.0 comes with increased risk. Contractors submitting false claims about their cybersecurity compliance can face penalties under the False Claims Act (FCA). This raises the stakes for organizations, making accurate documentation and transparent processes more critical than ever.
What Contractors Need to Do
Step 1: Understand Your Level
Determine which CMMC level applies to your organization based on the type of information you handle. For most contractors working with CUI, Level 2 will be the target.
Step 2: Perform a Gap Analysis
Conduct a readiness assessment to identify where your current cybersecurity practices fall short of NIST SP 800-171 requirements. This analysis should map out each control and provide a roadmap for remediation.
Step 3: Develop a System Security Plan (SSP) and POA&M
- SSP: A detailed document describing how your organization implements security controls.
- POA&M (Plan of Action and Milestones): Outlines gaps and a timeline for addressing them.
These documents are not optional as they are essential for demonstrating compliance during an assessment.
Step 4: Implement Technical and Procedural Controls
From multi-factor authentication to incident response policies, your organization must not only implement but also enforce and document required controls.
Step 5: Prepare for Self-Assessment or Third-Party Assessment
If your organization falls under Level 1 or certain Level 2 contracts, you will conduct an annual self-assessment. Otherwise, engage a C3PAO (Certified Third-Party Assessor Organization) to schedule and complete your review.
Common Challenges in Meeting CMMC 2.0
- Underestimating Documentation Needs
Technical controls are only half the battle. Without detailed policies, procedures, and proof of enforcement, organizations risk failing assessments. - Budgeting and Resource Allocation
Small and mid-sized contractors often lack the dedicated cybersecurity staff to maintain compliance. Partnering with an MSP or MSSP familiar with CMMC can fill this gap. - Managing Continuous Compliance
CMMC is not a one-time project. Contractors must maintain compliance year-round, update SSPs and POA&Ms, and stay current with evolving DoD requirements.
Benefits of Compliance Beyond DoD Contracts
While compliance may feel like a regulatory burden, CMMC 2.0 offers several organizational benefits:
- Enhanced Security Posture: Stronger defenses reduce the risk of costly breaches.
- Competitive Advantage: Compliance demonstrates credibility and can be a differentiator in winning contracts.
- Operational Efficiency: Structured security frameworks often lead to improved processes and accountability.
Conclusion
CMMC 2.0 marks a significant step forward in securing the Defense Industrial Base. By reducing levels, aligning with NIST, and balancing assessments between self-attestation and third-party reviews, the DoD has created a more streamlined but still rigorous framework.
For contractors, the key to success lies in preparation: understanding requirements, closing gaps, and maintaining continuous compliance. Organizations that embrace the changes proactively will not only remain eligible for DoD contracts but also strengthen their overall security posture in a threat-filled landscape.