AgileDefend™ Support delivers 24×7 U.S.-based IT helpdesk operations, Microsoft GCC High lifecycle management, and CMMC compliance oversight through a DFARS-aligned service framework. Integrated within SecureITSM’s zero-trust IT ecosystem, our ITIL-driven processes combine endpoint protection, ticket automation, and continuous compliance monitoring ensuring every incident, asset, and control remains secured, documented, and audit-ready.
Professional IT Service Desk Support — Built for Security, Compliance, and Speed
AgileDefend™ Support delivers mission-critical service desk operations within your Microsoft GCC High environment, uniting ITIL v4 processes, Zero Trust access control, and CMMC-aligned incident management. Each request flows through a compliance-aware chain, linking technical resolutions with your System Security Plan (SSP) and DFARS 252.204-7012 evidence trail. Integrated with Microsoft 365, Intune, and Azure, AgileDefend™ automates validation, escalation, and documentation ensuring every action is secured, traceable, and audit-ready.

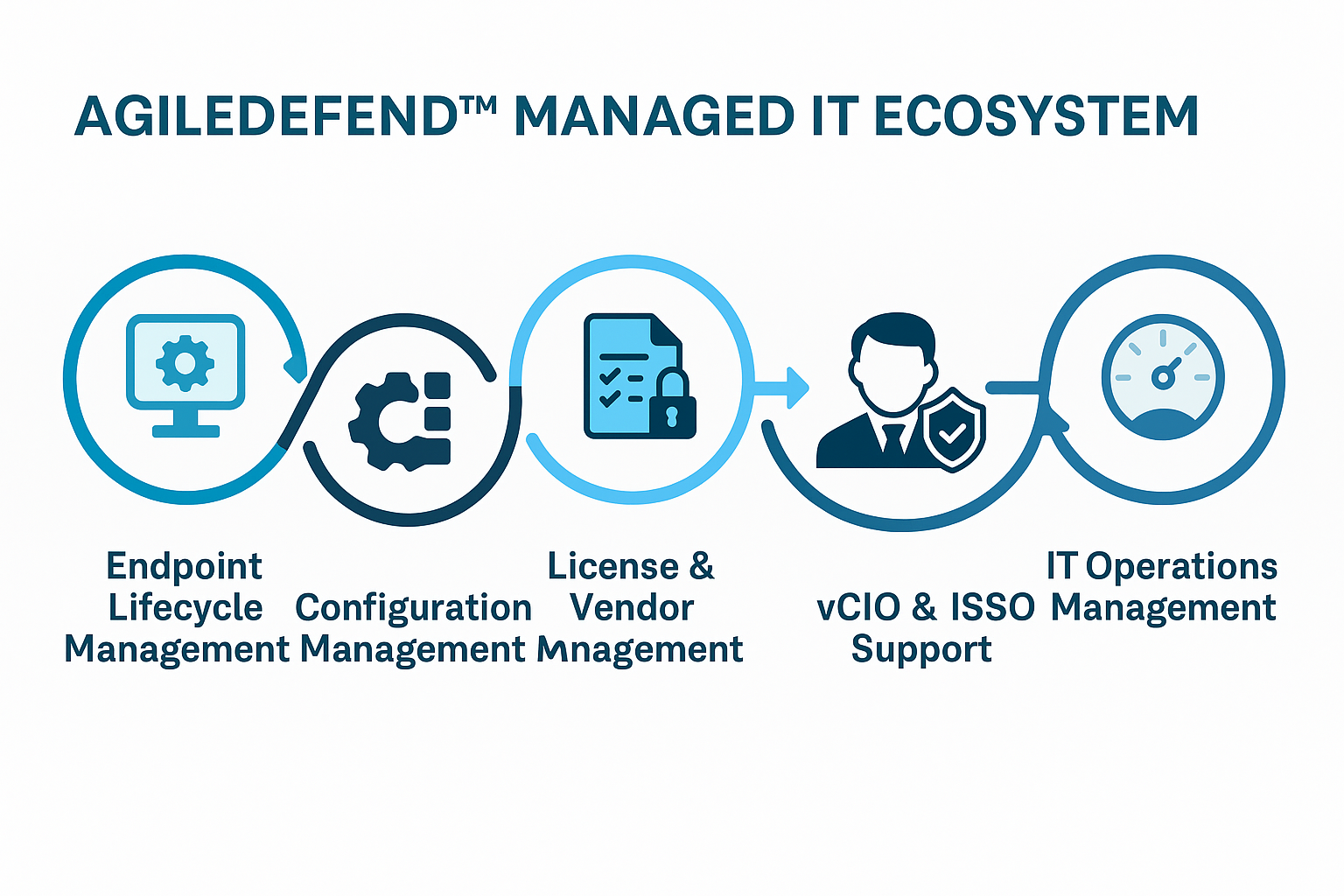
AgileDefend™ Support delivers an end-to-end managed IT framework that unifies cybersecurity, compliance, and operational oversight across every system. Built for Microsoft GCC High and DoD contractors, it ensures continuous visibility, patch validation, and lifecycle optimization, all mapped to CMMC and DFARS standards.
Centralized patch deployment, configuration baselining, and vulnerability tracking across all endpoints and mobile assets. Enforces compliance with CIS, NIST 800-171, and CMMC Level 2 configuration requirements.
Automated enforcement of system baselines tied to DFARS 252.204-7012 and CMMC CM.2.064 controls.
Ensures every configuration change is versioned, documented, and validated for audit readiness.
Maintain full control over software entitlements, renewals, and vendor compliance. Integrated reporting ensures each product remains licensed, supported, and security-patched.
Strategic governance and compliance oversight through Virtual CIO and Information System Security Officer (ISSO) services. Aligns business goals with cyber security maturity and long-term technology planning.
24×7 monitoring of servers, cloud infrastructure, and user endpoints with SLA-driven metrics and risk visibility dashboards. Delivers complete transparency into up time, performance, and compliance posture.
Service Desk Support Performance Metrics & Proven Results
Our comprehensive CMMC approach delivers measurable benefits across all aspects of compliance and security.
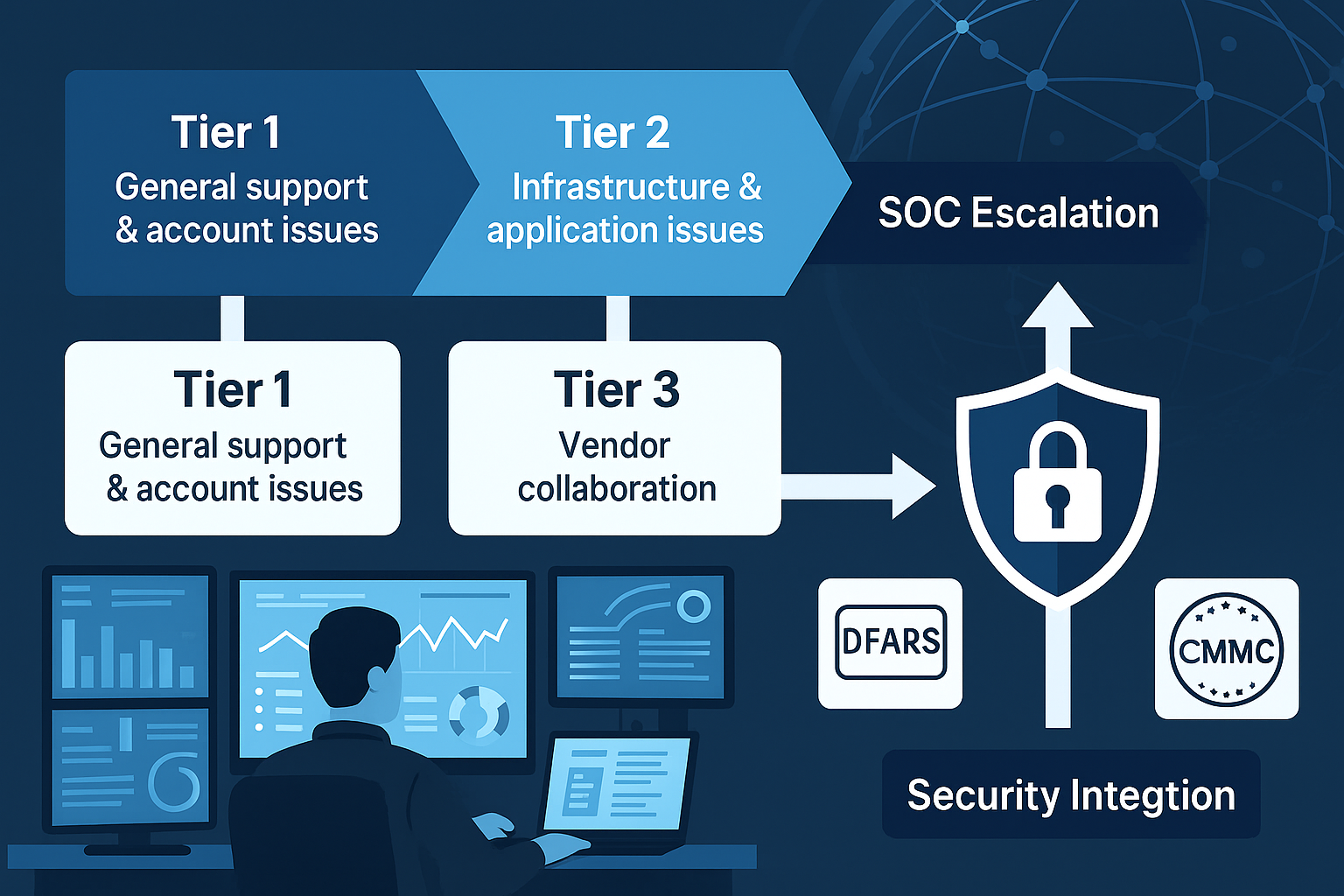
Every support incident within AgileDefend™ Support follows a tiered escalation framework engineered for precision, traceability, and compliance assurance. Integrated with SecureITSM’s SOC and Microsoft Sentinel telemetry, each escalation stage enforces Zero Trust access controls and DFARS-aligned documentation for end-to-end visibility.
Handles user-facing requests such as password resets, MFA troubleshooting, and secure access verification within GCC High. Every ticket is verified against Conditional Access policies, ensuring zero unauthorized resets and full CMMC AC.1.001 alignment.
Focuses on system performance, patch deployment, and Microsoft 365/Azure application issues. Engineers implement configuration baselines and validate all remediation steps through Intune and Defender XDR telemetry ensuring no control drift or compliance deviation.
Engages SecureITSM’s senior architects, compliance officers, and vendor liaisons for complex cases involving platform integrations, API failures, or compliance interpretation. All Tier 3 actions are version-controlled and tied to SSP evidence trails.
Potential threats or anomalous behaviors trigger immediate escalation to the SecureITSM Security Operations Center. SOC analysts perform Sentinel-based correlation, threat containment, and DFARS 252.204-7012 reporting workflows within 15 minutes of detection.
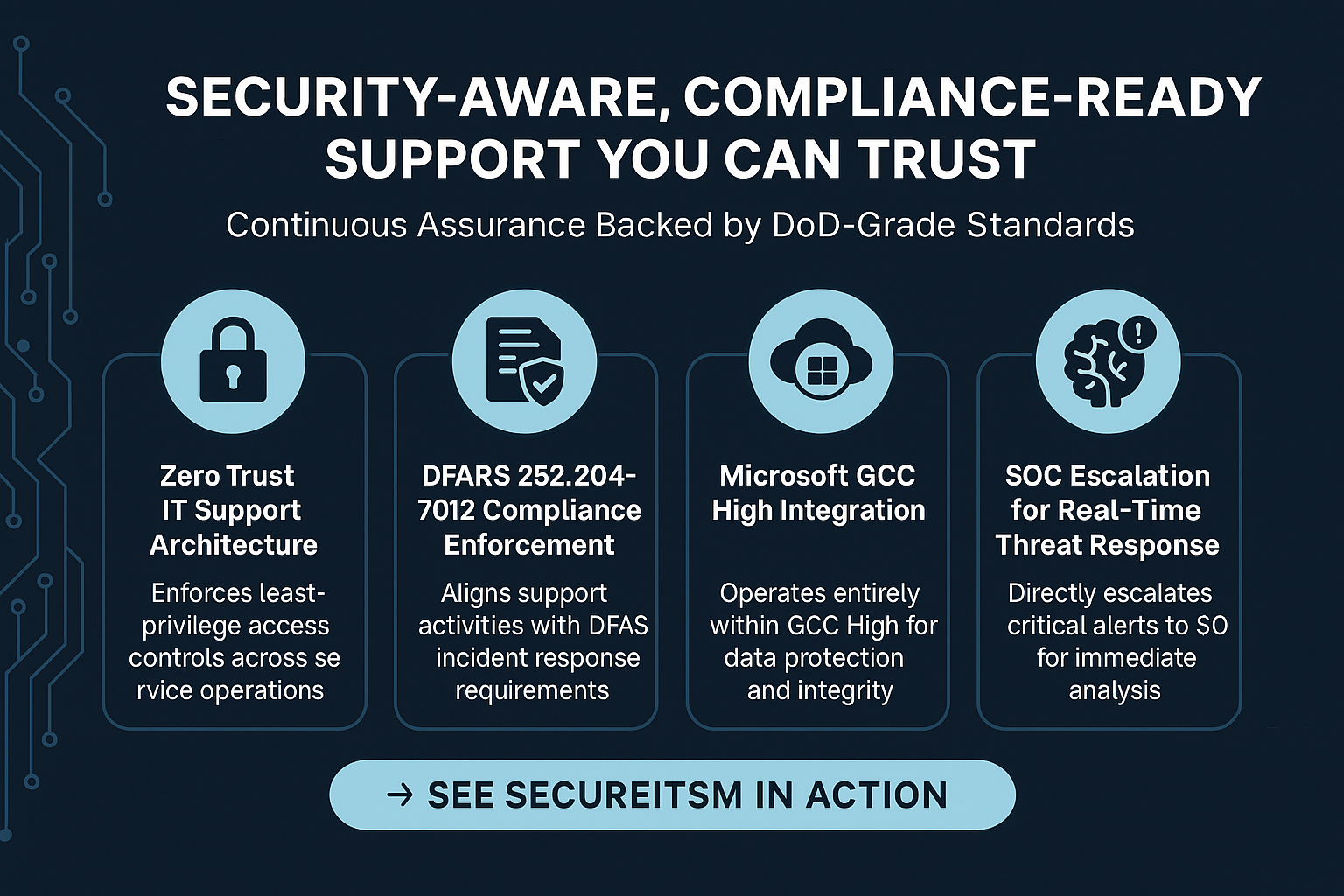
Every SecureITSM support process from identity provisioning to patch deployment is engineered to meet the most stringent federal cybersecurity frameworks, including DFARS 252.204-7012, CMMC Level 2, and NIST 800-171A. Our AgileDefend™ Support architecture integrates Zero Trust enforcement, GCC High workflows, and automated compliance telemetry ensuring every IT action is secure, traceable, and audit-validated.
SecureITSM’s service desk enforces Zero Trust across every endpoint and identity transaction. Access is governed by Conditional Access in Microsoft Entra ID, ensuring least-privilege authentication and verified device posture before escalation or resolution.
All service operations and ticket workflows are aligned with DFARS data protection and incident reporting standards. Evidence artifacts and ticket histories are version-controlled to maintain 100% audit traceability across incident handling.
Native integration with Microsoft GCC High enables end-to-end encryption, compliant data residency, and seamless synchronization of logs, alerts, and configuration baselines for defense contractors under ITAR and DFARS constraints.
Every incident is monitored by our integrated Security Operations Center, leveraging Microsoft Sentinel and Defender XDR telemetry for real-time correlation, alert triage, and post-incident forensics ensuring threats are contained before escalation.

Partner with SecureITSM for 24×7 managed IT and compliance-driven service desk operations. Stay continuously compliant with AgileDefend™ Support, built to meet CMMC and DFARS standards. We go beyond ticket resolution ensuring mission-critical uptime, compliance integrity, and verifiable control documentation.