With cyber threats evolving rapidly, organizations must prioritize cybersecurity and continuously monitor their security posture. A Security Operations Center (SOC) plays a crucial role in detecting, analyzing, responding to, and mitigating cyber threats. However, not all businesses can afford to establish an in-house SOC due to resource constraints. Fortunately, they can still benefit from a Managed SOC (or SOC as a Service).
What is a SOC?
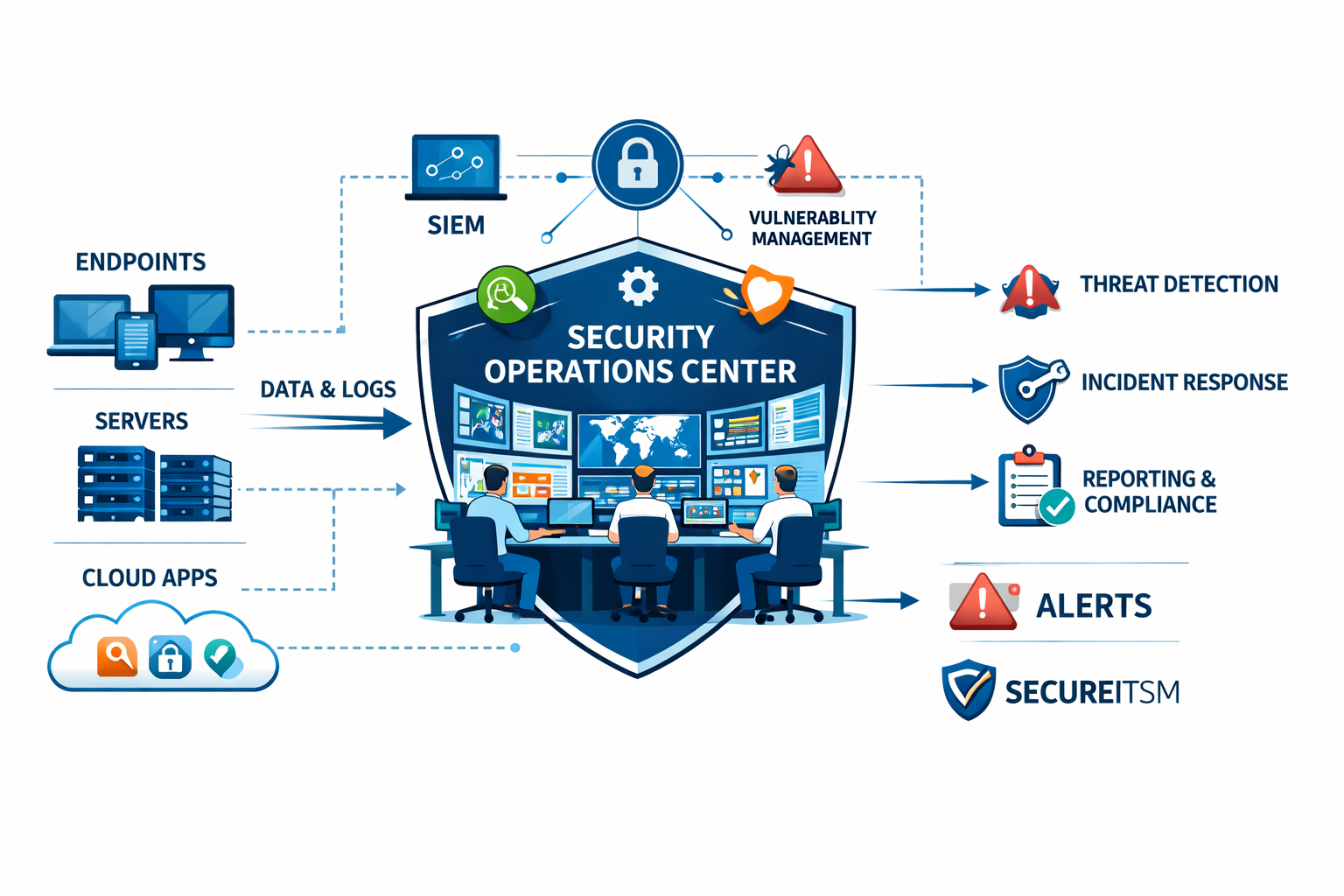
A Security Operations Center (SOC) is a team of IT security professionals dedicated to real-time cyber threat monitoring, detection, and response. Whether in-house or outsourced, a SOC oversees an organization's entire IT infrastructure, analyzing event logs and responding to security incidents to safeguard against cyberattacks.
Security operations centers are critical for improving threat monitoring, detection, and response capabilities of an organization. They provide vital support in identifying, protecting against, and addressing threats such as phishing, malware, data breaches, insider threats, supply chain attacks, DoS/DDoS attacks, and cyber-espionage.
Key SOC Functions
The SOC's primary goal is to maintain an organization's cybersecurity technologies while also working to improve its overall security posture. The SOC team is in charge of managing the daily operational activities connected with an enterprise's network and infrastructure security. In addition to their main focus of detecting, analyzing, and responding to threats, members of a SOC team may also contribute to developing the security strategy or designing the security architecture with their knowledge and expertise. The key functions of a SOC include:
- Managing security tools, patches, and updates
- Monitoring IT infrastructure for threats
- Collecting and analyzing cyber threat intelligence
- Investigating and containing security incidents
- Recovering compromised data and assets
- Enhancing security monitoring tools
- Ensuring compliance and risk management
Types of SOC Models
- In-House SOC – Fully managed internally, providing complete control but requiring significant investment in technology and personnel.
- Outsourced SOC – A third-party service provider manages security monitoring, offering a cost-effective, scalable solution with reduced internal oversight.
- Hybrid SOC – A combination of internal and outsourced resources, balancing control with external expertise.
What is a Managed SOC?
A Managed SOC, also known as SOC as a Service, is a subscription-based solution where a third-party provider oversees an organization's cybersecurity. These providers offer threat detection, incident response, and security management services, enabling businesses to access expert security support without investing in an in-house team.
Benefits of a Managed SOC
- 24/7 Monitoring: A Managed SOC ensures 24/7 surveillance of an organization’s network, systems, and applications to detect potential security threats, allowing for swift identification and resolution of security incidents.
- Expert Support: With a Managed SOC, organizations benefit from seasoned security professionals who possess the skills, knowledge, and experience needed to effectively detect and mitigate security threats.
- Threat Detection & Response: Utilizing advanced security tools and technologies, a Managed SOC swiftly identifies threats and responds proactively, reducing the impact of security incidents and helping prevent future attacks.
- Regulatory Compliance: A Managed SOC supports organizations in meeting compliance requirements by offering continuous monitoring, incident response, and comprehensive reporting capabilities.
Managed SOC vs. MSSP
A Managed SOC focuses on real-time security operations, including monitoring, threat hunting, and incident response. In contrast, a Managed Security Services Provider (MSSP) offers broader cybersecurity services, including firewall management and vulnerability scanning. While both provide security solutions, a Managed SOC delivers deeper, more focused protection.
Managed SOC Pricing & Factors
Pricing varies based on factors like service scope, technology stack, compliance needs, and vendor reputation. Common pricing models include:
- Per-device or per-user pricing – Fixed cost per monitored asset.
- Tiered pricing – Different service levels based on monitoring and response needs.
- Event-based pricing – Cost based on the volume of security incidents.
- Subscription-based pricing – Fixed periodic fees regardless of activity levels.
Establishing Security Baselines:
We establish and maintain the following security baselines:
Microsoft Tenant: Your tenant’s security must be cross-coordinated and configured using 365 Admin Center, Intune, Entra, Cloud App, Compliance Policies, Log Analytics, Attack Surface Reduction, etc. The average MS Tenant requires 4,000 discrete configuration settings.
Windows Computers: This security baseline is established using six (6) different Intune security baselines plus the Windows 11 STIG.
Servers: Server baselines are established for Windows and Linux servers using DoD STIGs. Access control is limited, system hardening occurs, and log creation is implemented.
Networking Equipment: Firewalls, switches, etc. baselines are configured using DoD STIGs. There are specific configuration for all standard networking equipment.
Baseline Management: Baselines are ever evolving. Microsoft baselines are normally updated 2x a year while computer, server, and networking equipment baselines are normally updated 3x to 4x times a year. We maintain and update your baselines as required. New baselines are put into production monthly.
SecureITSM’s Managed SOC Services include:
- Log Management & Monitoring: SecureITSM provides continuous log collection and 24/7 event log monitoring, ensuring early threat detection while meeting regulatory and forensic requirements.
- Threat Detection: Our advanced security analytics leverage AI and contextual analysis and a robust big data platform powered by threat intelligence services to effectively detect and respond to threats.
- Incident Response Services: Whether onsite or remote, our incident responders collaborate with your IT and business teams to contain threats, conduct thorough damage assessments, and implement response plans.
- Malware Analysis & Forensics: In critical investigations, our digital experts leverage advanced forensic techniques to identify, analyze, and mitigate malware threats.
- Service Management & Reporting: Through our secure portal, you can report incidents, request services, and track ticket statuses. Our SOC analysts ensure swift resolution while providing updates on severity levels, work logs, and actions taken. You receive specialized reports (daily, weekly, or monthly) on key security metrics such as top infected systems, failed login attempts, and leading threat sources.
- Comprehensive Vulnerability Management: SecureITSM follows a structured approach—monitor, assess, prioritize, prevent, and remediate—to deliver thorough vulnerability management. By integrating with vulnerability assessment scanners, we generate timely alerts and detect compliance deviations from baseline security standards.
- Threat Intelligence Services: Our team aggregates and correlates thousands of security events using a multi-tenant Security Information and Event Management (SIEM) platform, supported by real-time threat feeds. You also gain access to threat advisory reports, offering insights into critical vulnerabilities and recent malware activity.
The SecureITSM Benefit
Our services help you reduce risk and improve your organization's security posture with:
- An integrated security framework: With consolidated security options for vulnerability management, threat feed, forensic analysis, malware analysis, and so on, you can make better security decisions with intelligence-driven analytics.
- Effective monitoring and visibility: Our scalable log management system streamlines and optimizes the collation of logs across devices and locations. TCS' MSS Portal enables quick and easy access to real-time reports, giving you a comprehensive, in-depth view of your organization's security issues and vulnerabilities.
- Compliance with government and industry regulations: We help you establish a compliance baseline, and continually measure and manage against this. We provide detailed compliance and audit reports for the Sarbanes-Oxley (SOX) Act, General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), and other regulatory requirements.
- Service quality and responsive delivery: Our commitment to highest quality standards, customer centric service delivery, and SLA-governed deliverables ensure complete transparency and quality.
- Flexible options: You can choose a service plan that matches your enterprise's requirements. We support legacy and home-grown applications as well, and integrate them with our applications. Our services are hosted on the cloud and are available in pay-as-you use models.
- Cost efficiency: By leveraging our hosted technologies platform, you can address security requirements in a cost-optimal manner. The platform and methodologies help quick provisioning of services to meet your business requirements.
The SecureITSM Advantage
By partnering with SecureITSM, companies can take advantage of:
- Domain expertise: SecureITSM’s team of security professionals have extensive experience in executing complex assignments. Performance is driven by metrics and service level agreements (SLAs) to ensure tangible outcomes.
- Unique delivery model: Our delivery model is based on the Information Technology Infrastructure Library (ITIL), and we deliver consistent round-the-clock support at lower cost.
- STIG Experts: SecureITSM is an expert in decoding and implanting Security Technical Implementation Guides (STIG). STIGs are published by the US Department of Defense (DoD) which manages the cybersecurity of 10M plus endpoints. STIGs help organizations secure their systems, software, and networks against threats and vulnerabilities. STIGs provide advanced security configuration guidance on 400 plus topics.